This NIVIDIA security bulletin was originally published on 8th Feb 2024.
CVE-2023-31031 was released by NIST on January 12, 2024. But what were the design flaws found in SBIOS? Officials stated that the flaw will lead to a stack-based buffer overflow in local access.
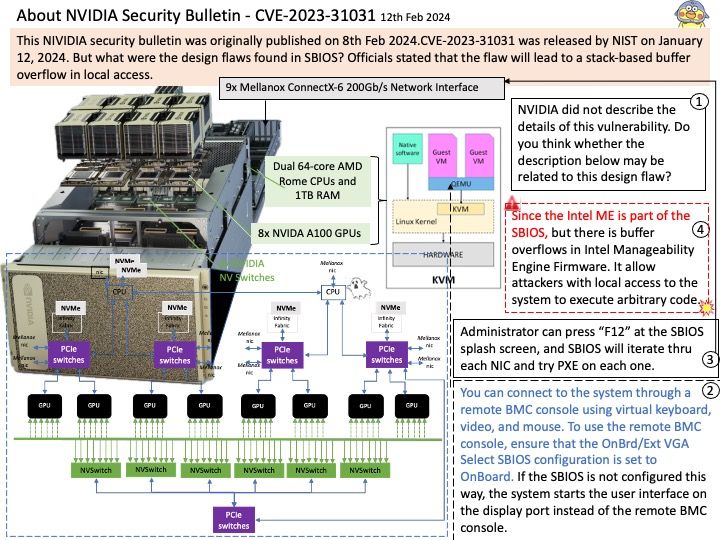
Preface: NVIDIA did not describe the details of this vulnerability. Do you think whether the description on attached diagram (step 4) may be related to this design flaw?
Background: Because the SBIOS update is accomplished in two phases (main SBIOS update first, followed by the Intel ME update), you will need to power cycle the server a couple of times to update all the components.
Updating the SBIOS Certificate
1.Obtain the CA certificate from the signing authority that was used to sign the SSL certificate.
2.Copy the CA certificate onto a USB thumb drive or to /boot/efi on the A100 OS.
3.Access the DGX A100 console from a locally connected keyboard and mouse or through the BMC remote console.
4.Reboot the server
Ref: Memory on the heap is dynamically allocated at runtime and typically contains program data.
Vulnerability details: NVIDIA DGX A100 SBIOS contains a vulnerability where a user may cause a heap-based buffer overflow by local access. A successful exploit of this vulnerability may lead to code execution, denial of service, information disclosure, and data tampering.
Official details: Please refer to the link for details –