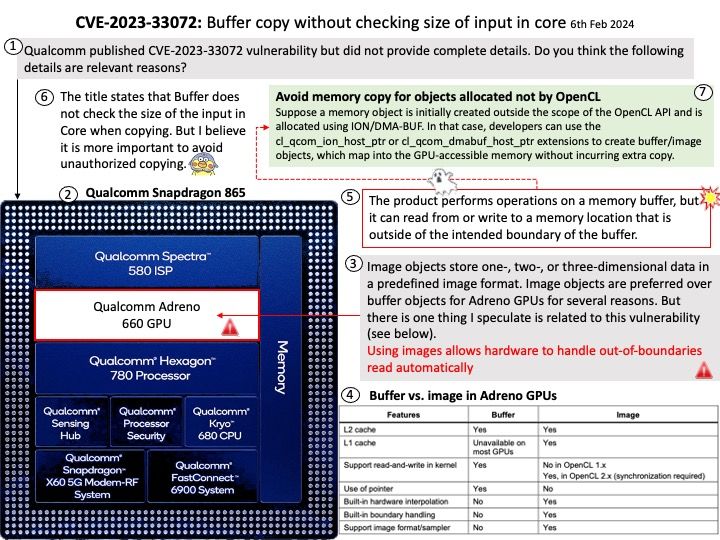
Preface: The title states that Buffer does not check the size of the input in Core when copying. But I believe it is more important to avoid unauthorized copying.
Background: An OpenCL Buffer is a 1D or 2D or 3D array in global memory. Its an abstract object that can be addressed thru a pointer. Buffers are Read-Only or Write_only or Read-Write. An Image buffer represents GPU Texture memory. It represents an array of pixels that can be access via functions specifying pixel x,y,z coordinates. There is no pointer access to Image Pixels on the GPU.
OpenCL supports buffer and image objects (and pipe objects from OpenCL 2.0). The one-dimensional buffer objects are a natural choice for many developers due to their simplicity and flexibility, such as the support of pointers, byte-addressable access, etc. For instance, using images allows hardware to handle out-of-boundaries read automatically.
Ref: An OpenCL Buffer is a 1D or 2D or 3D array in global memory. Its an abstract object that can be addressed thru a pointer. Buffers are Read-Only or Write_only or Read-Write. An Image buffer represents GPU Texture memory. It represents an array of pixels that can be access via functions specifying pixel x,y,z coordinates. There is no pointer access to Image Pixels on the GPU.
Vulnerability details: The product performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer.
Date Reported 2022/12/20
Customer Notified Date 2023/08/07
Official details: Please refer to the link for details – https://docs.qualcomm.com/product/publicresources/securitybulletin/february-2024-bulletin.html