Preface: cURL command is an important Linux tool, commonly used for data transfer and connection troubleshooting.
Background: EC2 Instance – Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the Amazon Web Services (AWS) Cloud. Using Amazon EC2 eliminates your need to invest in hardware up-front so that you can develop and deploy applications faster.
Best Practices for Building AMI:
Check port settings as follows:
- Linux-based AMIs – Ensure that a valid SSH port is open. The default SSH port is 22.
- Windows-based AMIs – Ensure that an RDP port is open. The default RDP port is 3389. Also, the WinRM port (5985 by default) must be open to 10.0.0.0/16.
Ensure that your AMI meets all AWS Marketplace policies, including disabling root login.
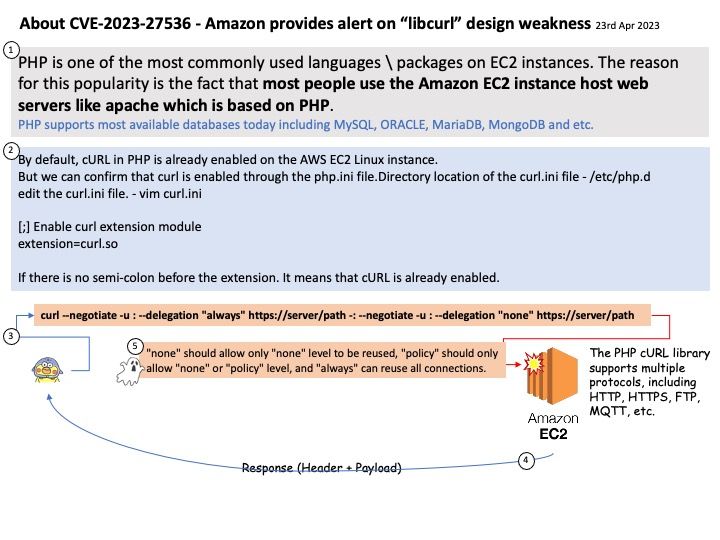
Vulnerability details: An authentication bypass vulnerability exists libcurl <8.0.0 in the connection reuse feature which can reuse previously established connections with incorrect user permissions due to a failure to check for changes in the CURLOPT_GSSAPI_DELEGATION option. This vulnerability affects krb5/kerberos/negotiate/GSSAPI transfers and could potentially result in unauthorized access to sensitive information. The safest option is to not reuse connections if the CURLOPT_GSSAPI_DELEGATION option has been changed.
Official details: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-27536