Preface: FreeSWITCH is a Software Defined Telecom Stack enabling the digital transformation from proprietary telecom switches to a versatile software implementation that runs on any commodity hardware.
Background: FreeSWITCH listens on port 8021 by default and will accept and run commands sent to it after authenticating. By default commands are not accepted from remote hosts.
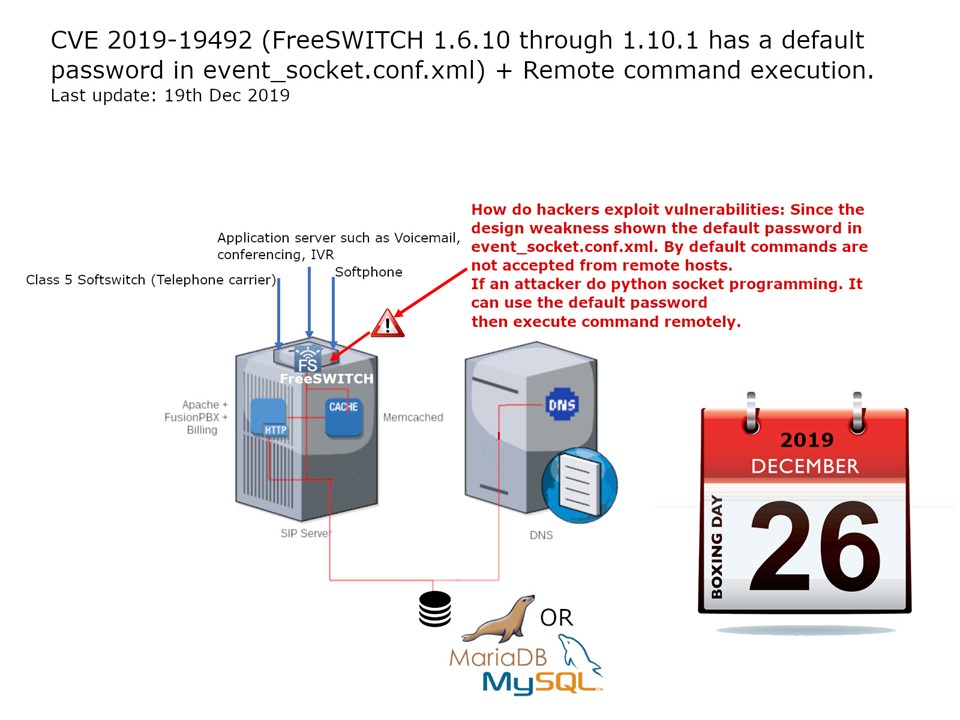
Design weakness: FreeSWITCH 1.6.10 through 1.10.1 has a default password in event_socket.conf.xml. How do hackers exploit vulnerabilities: Since the design weakness shown the default password in event_socket.conf.xml. By default commands are not accepted from remote hosts. If an attacker do python socket programming. It can use the default password and excute the command remotely.
Remedy: It is recommended to block all untrusted python socket connections with a firewall on this device until the vendor provides an official patch.