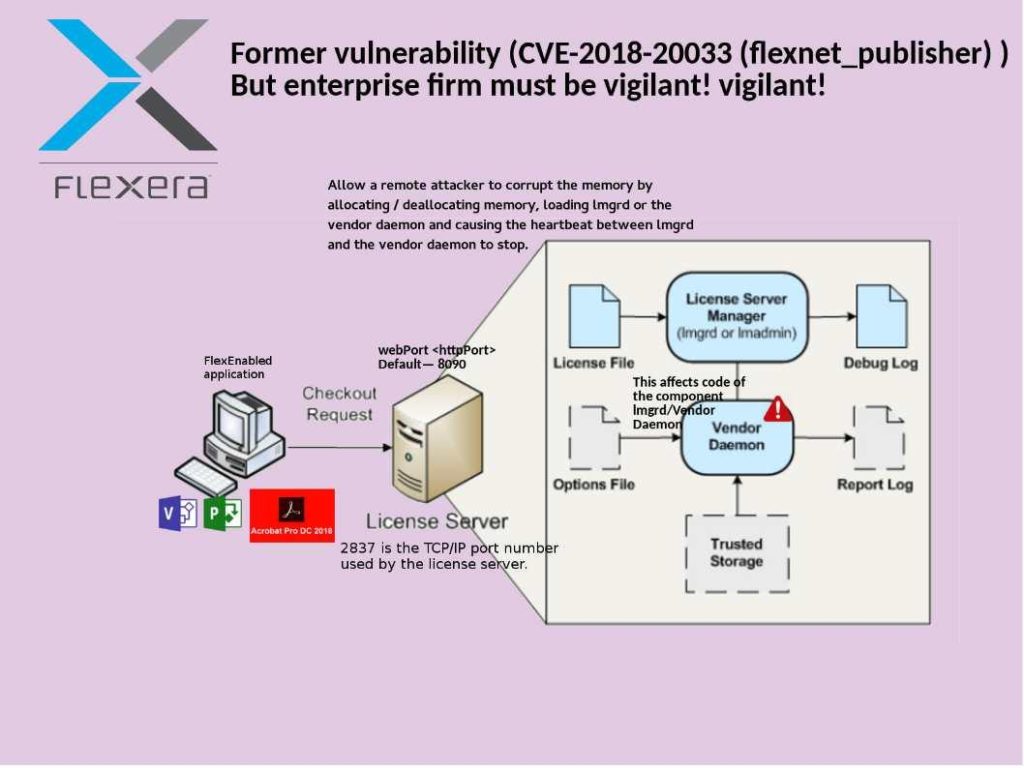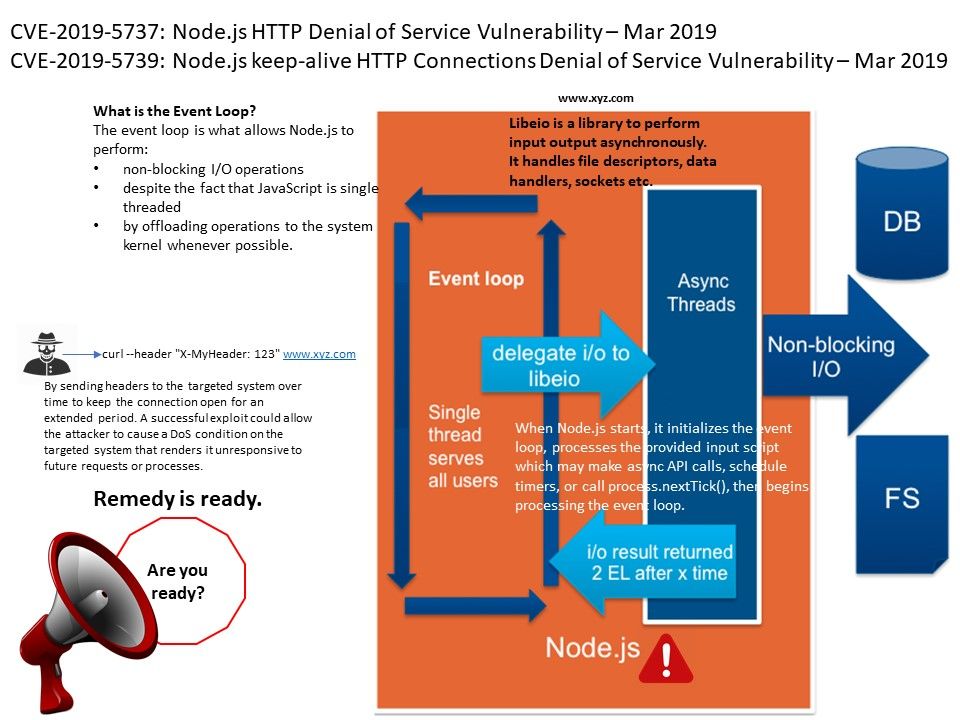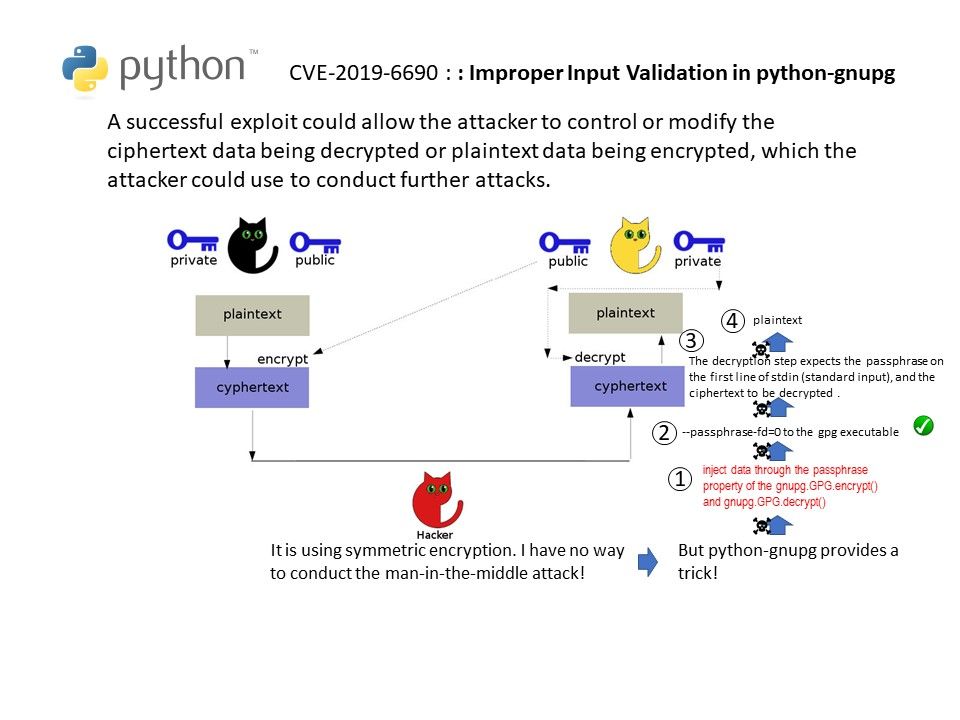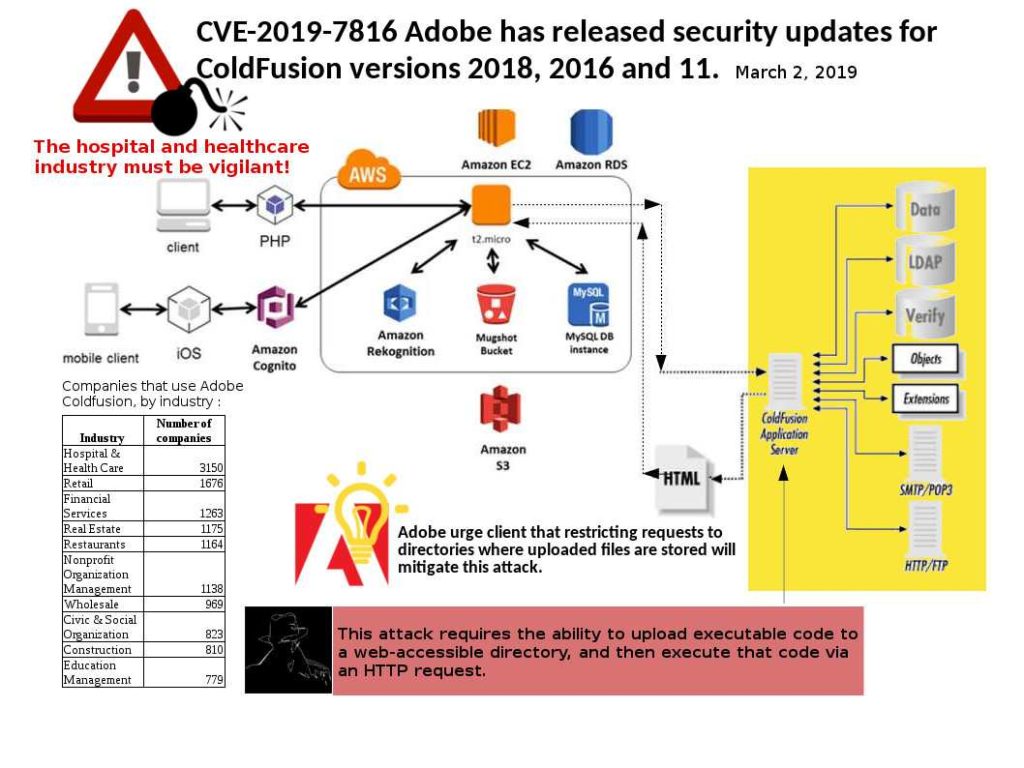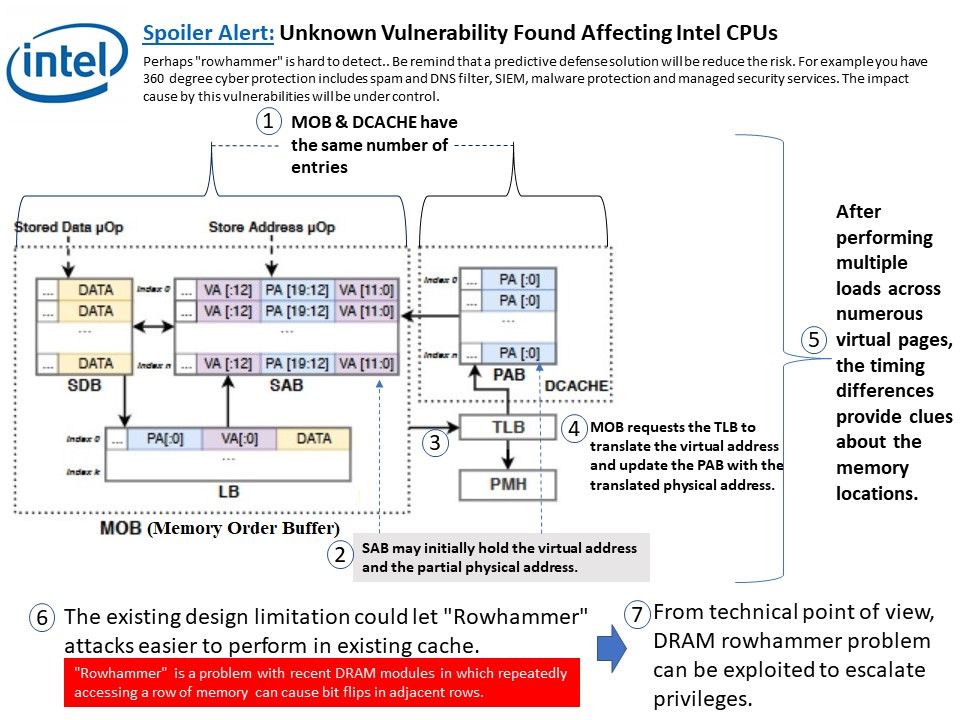
Preface: So called Spoilter, a vulnerability given by Intel CPU design limitation. If hacker successful exploit such vulnerability. They can conduct “Rowhammer” attack for privileges escalation.
Vulnerability detail: The speculative execution function of Intel’s processors aim to increase the performance of a CPU. Meanwhile it caused Intel CPU vulnerability issues in the past. A new found technique is able to determine how virtual and physical memory is related to each other. By discovering time differences, an attacker can determine the memory layout and then know which area to attack. For more details, please refer attached diagram for reference.
Remedy: There is no mitigation plan that can completely erase this problem.
Headline news: https://www.theregister.co.uk/2019/03/05/spoiler_intel_processor_flaw/
Conclusion: Perhaps “rowhammer” is hard to detect.. Be remind that a predictive defense solution will be reduce the risk. For example you have 360 degree cyber protection includes spam and DNS filter, SIEM, malware protection and managed security services. The impact cause by this vulnerabilities will be under control.