Preface: Node.js is popular in technology world. No matter crypto or distributed ledger platform, Docker development, REST API…etc can deploy by node.js.
About node.js?
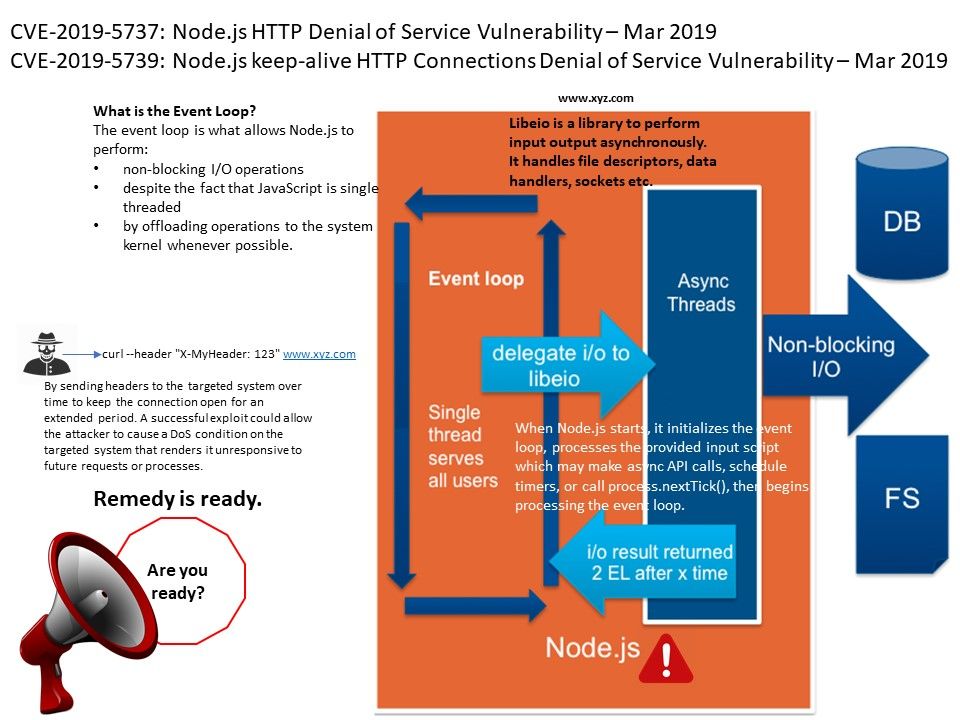
Node.js is a JavaScript runtime environment that processes incoming requests in a loop, called the event loop (initialization and callbacks) and offers a Worker Pool to handle expensive tasks like file I/O. Modern kernel can handle multiple operations executing in the background. Node.js design aim to let’s kernel tells Node.js so that the appropriate callback may be added to the poll queue to eventually be executed. Perhaps such design concept provides an opportunity to hacker!
Vulnerability details (CVE-2019-5737): An attacker could exploit this vulnerability when establishing an HTTP or HTTPS connection in keep-alive mode by sending headers to the targeted system over time to keep the connection open for an extended period. As a result a denial of service condition occurred. Official announcement display in below url: https://nodejs.org/en/blog/vulnerability/february-2019-security-releases/