Linux (systemd) current status update – 7th Nov 2018
If you are the old folk. Perhaps you will familiar with (init)?
The trend is going to replace the old mechanism (init) with new one (systemd). From techincal point of view, people satisfy the techincal features of “systemd”. However they are concern that such design are all in one place (package). Even though text book mentioned in theory so called trusted kernel kernel. The overall infrastructure will be build by several components. The realistic told the world that no safe place in cyber world. If you would like to make yourself secure, it is better to get rid your electronic belongings. We all know it was not possible!
Background – What is “systemd”?
The parent of all other processes (directly or indirectly)
Which Linux brand now fully deployed with “systemd” instead of “init”?
Fedora, OpenSuSE, Arch, RHEL, CentOS, etc.
Vulnerability status:
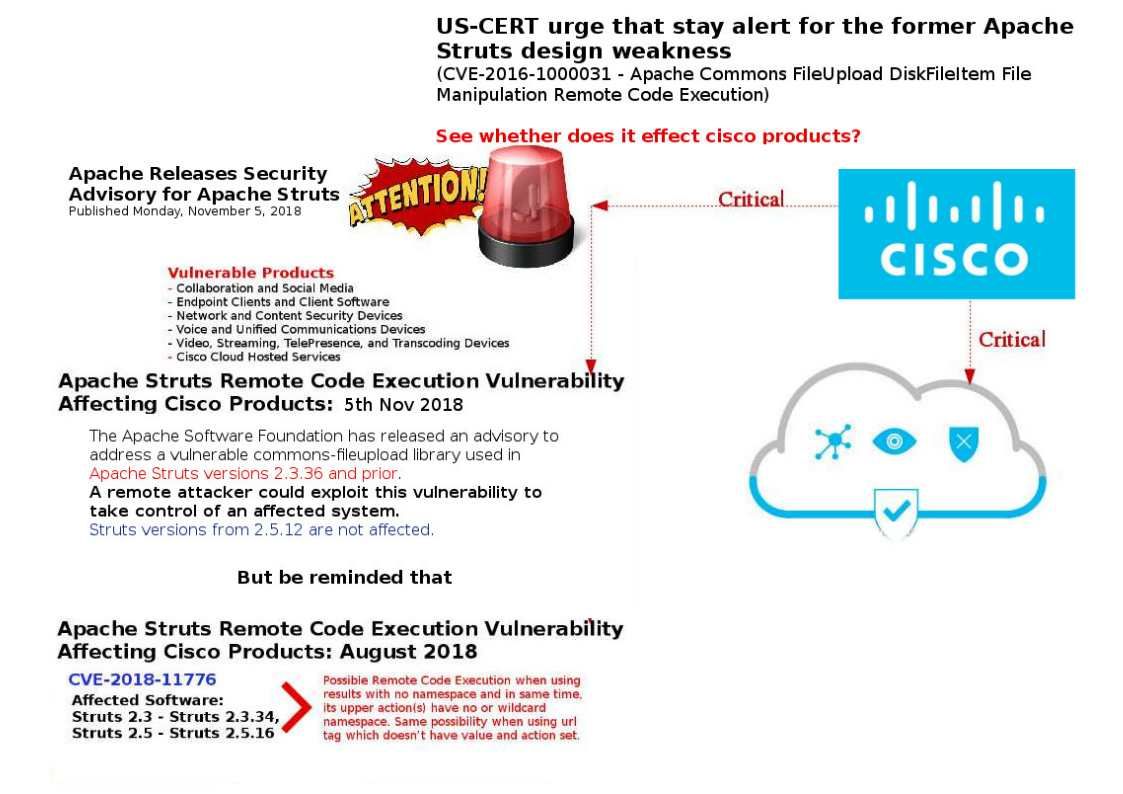
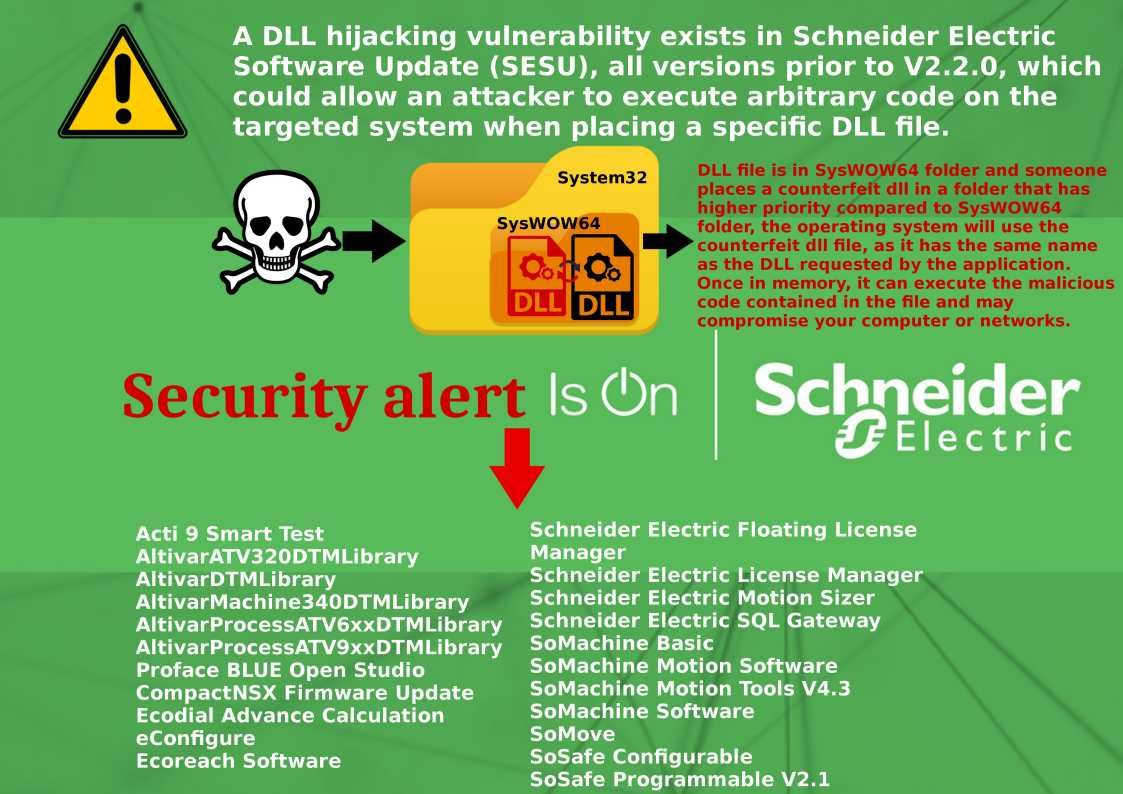
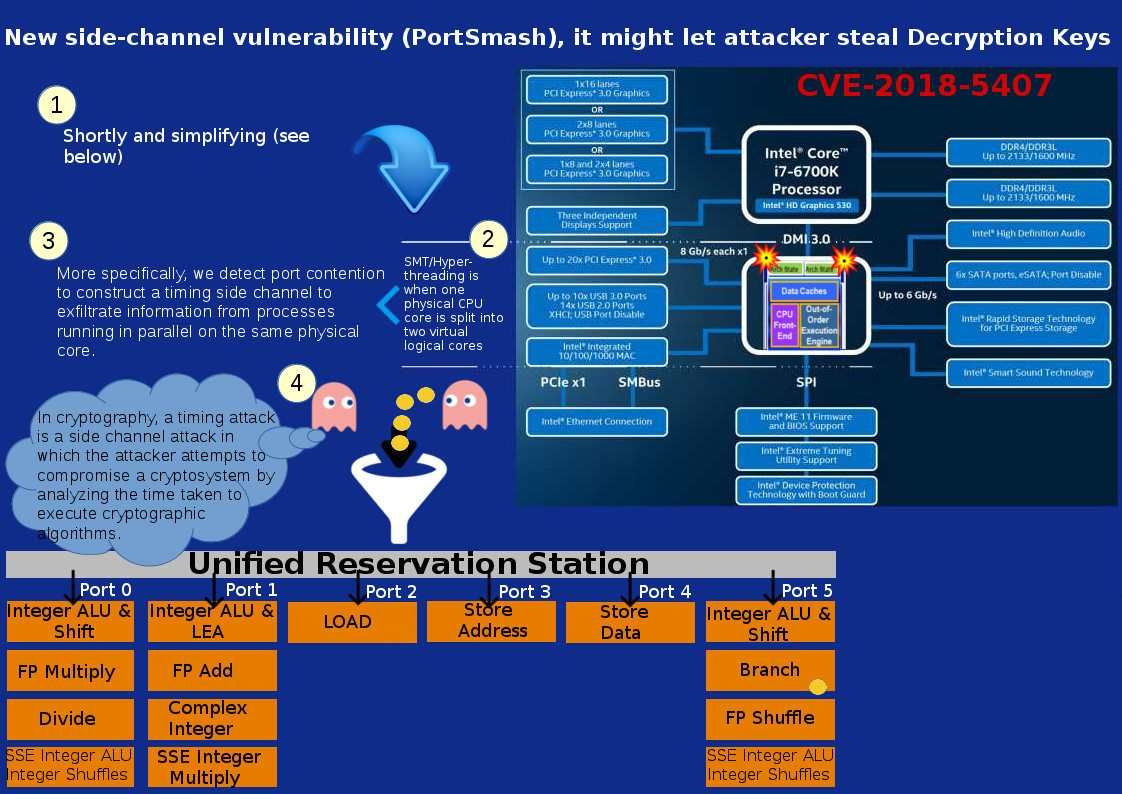
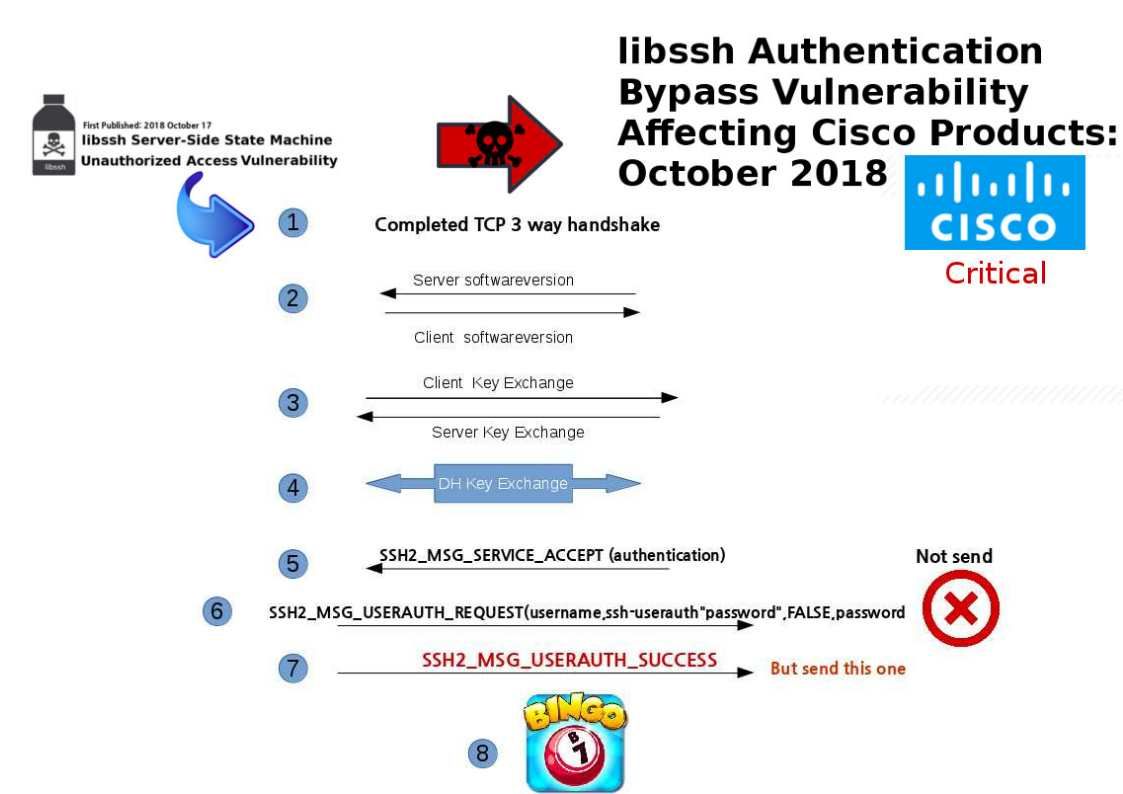
Refer attached diagram and below URL for references.
https://access.redhat.com/security/cve/cve-2018-15686
https://access.redhat.com/security/cve/cve-2018-15687
https://access.redhat.com/security/cve/cve-2018-15686
Conclusion: POSIX defined set of standards for an operating system or a program. But “systemd” not a POSIX standard. The computing system life cycle is really short today. It cannot compare with our home old day appliances.