Preface:
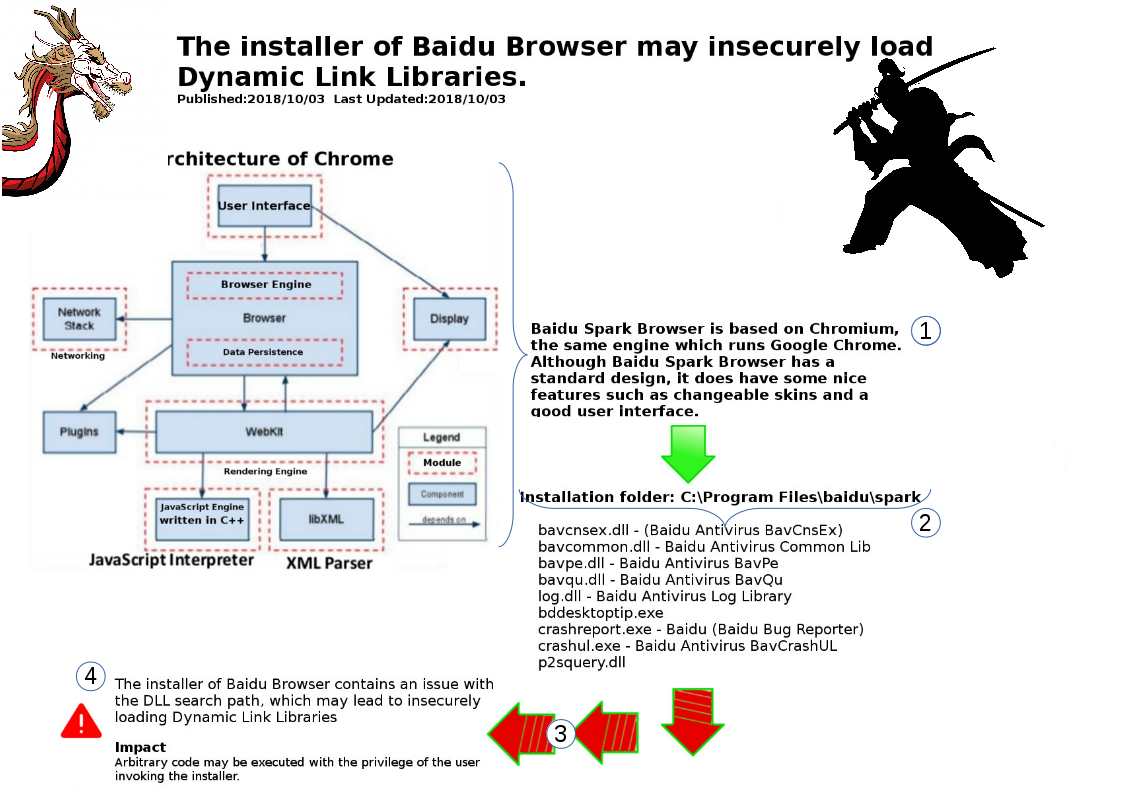
Baidu Spark Browser is based on Chromium, the same engine which runs Google Chrome.
Vulnerability findings:
Baidu Browser provided by Baidu, Inc. is a Web browser. The installer of Baidu Browser contains an issue with the DLL search path, which may lead to insecurely loading Dynamic Link Libraries.
Impact:
Arbitrary code may be executed with the privilege of the user invoking the installer.
Observation:
The threat actor can placing a malicious version of the dll file in the “C:\Program Files (x86)\baidu\spark\” folder. When the victim starts the browser, the browser execute file will load the malicious version of dll library file. How does the malicious dll file implant? It looks that a reserve engineering was happened in the original installer.
Reference URL:
Hi all, here every one is sharing these kinds of familiarity, so it’s pleasant to read this weblog, and I used to visit this blog every day.|