Preface: You found an error in somewhere, sometimes will be expanded your idea of thinking.
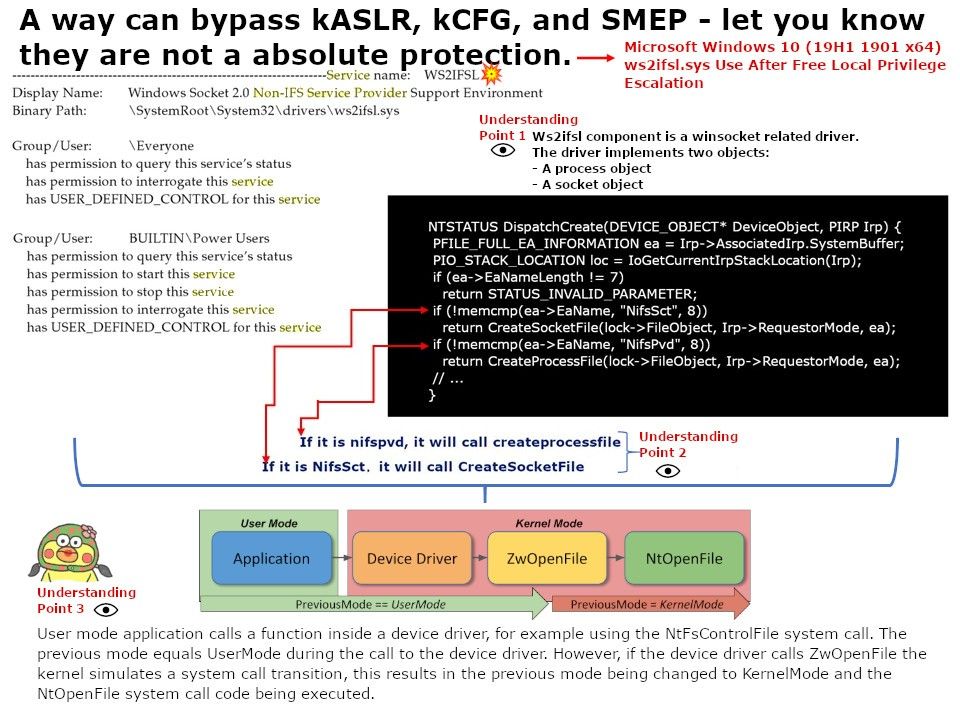
Synopsis: Ws2ifsl.sys is found in the C:\Windows\System32\drivers directory. In many cases, a driver creates a symbolic link and its name can be used as a file name for CreateFileA, but this is not the case with ws2ifsl. It only calls nt!IoCreateDevicewith the DeviceName set to ‘\Device\WS2IFSL’. IoCreateDevice creates a device object and returns a pointer to the object. The caller is responsible for deleting the object when it is no longer needed by calling IoDeleteDevice.
Vulnerability details: An elevation of privilege vulnerability exists in the way that ws2ifsl.sys (Winsock) handles objects in memory, aka ‘Windows Elevation of Privilege Vulnerability’. This CVE ID is unique from CVE-2019-1253, CVE-2019-1278, CVE-2019-1303.
Patch analysis: According to Microsoft patched version (10.0.18362.356). We can see the patched features:
– CreateProcessFile
– Delivery closed
– Signal cancelled
– Signal requirements
– RequestRundownRoutine
– CancelRundownRoutine
Under my observation: If a device name is not supplied (that is, DeviceName is NULL), the device object created by IoCreateDevice will not (and cannot) have a discretionary access control list (DACL) associated with it. Do you think this issue will give an oppuntunity let attacker to exploit?