Technical Background: How to manages a CDE session? The dtsession command provides session management functionality, compliant with ICCCM 1.1, during a user session, from login to logout. It starts a window manager and allows users to save a session, restore a session, lock a session, start screen savers, and allocate colors for desktop-compatible clients.
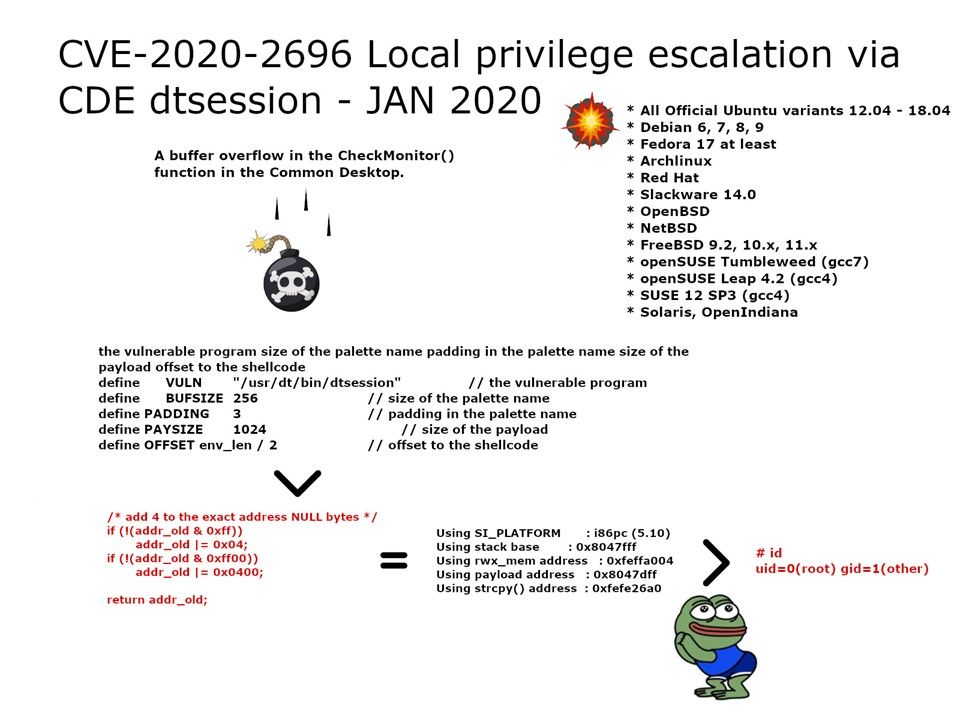
Vulnerability details: A buffer overflow in the CheckMonitor() function in the Common Desktop. It allows local users to gain root privileges via a long palette name passed to dtsession in a malicious .Xdefaults file (CVE-2020-2696).
- All Official Ubuntu variants 12.04 – 18.04
- Debian 6, 7, 8, 9
- Fedora 17 at least
- Archlinux
- Red Hat
- Slackware 14.0
- OpenBSD
- NetBSD
- FreeBSD 9.2, 10.x, 11.x
- openSUSE Tumbleweed (gcc7)
- openSUSE Leap 4.2 (gcc4)
- SUSE 12 SP3 (gcc4)
- Solaris, OpenIndiana
Remedy: The open source CDE 2.x version have issued the following patches for this vulnerability:
https://sourceforge.net/p/cdesktopenv/mailman/message/36900154/
https://sourceforge.net/p/cdesktopenv/code/ci/6b32246d06ab16fd7897dc344db69d0957f3ae08/