Preface: Preface: Threat Intelligence vendor (FireEye) alert that Global DNS Hijacking Campaign rapidly growth. This storm affected dozens of domains belonging to government, telecommunications and internet infrastructure entities across the Middle East and North Africa, Europe and North America.
Synopsis: More information about the impact of this cyber attack.. Please refer to below url for reference. https://www.fireeye.com/blog/threat-research/2019/01/global-dns-hijacking-campaign-dns-record-manipulation-at-scale.html
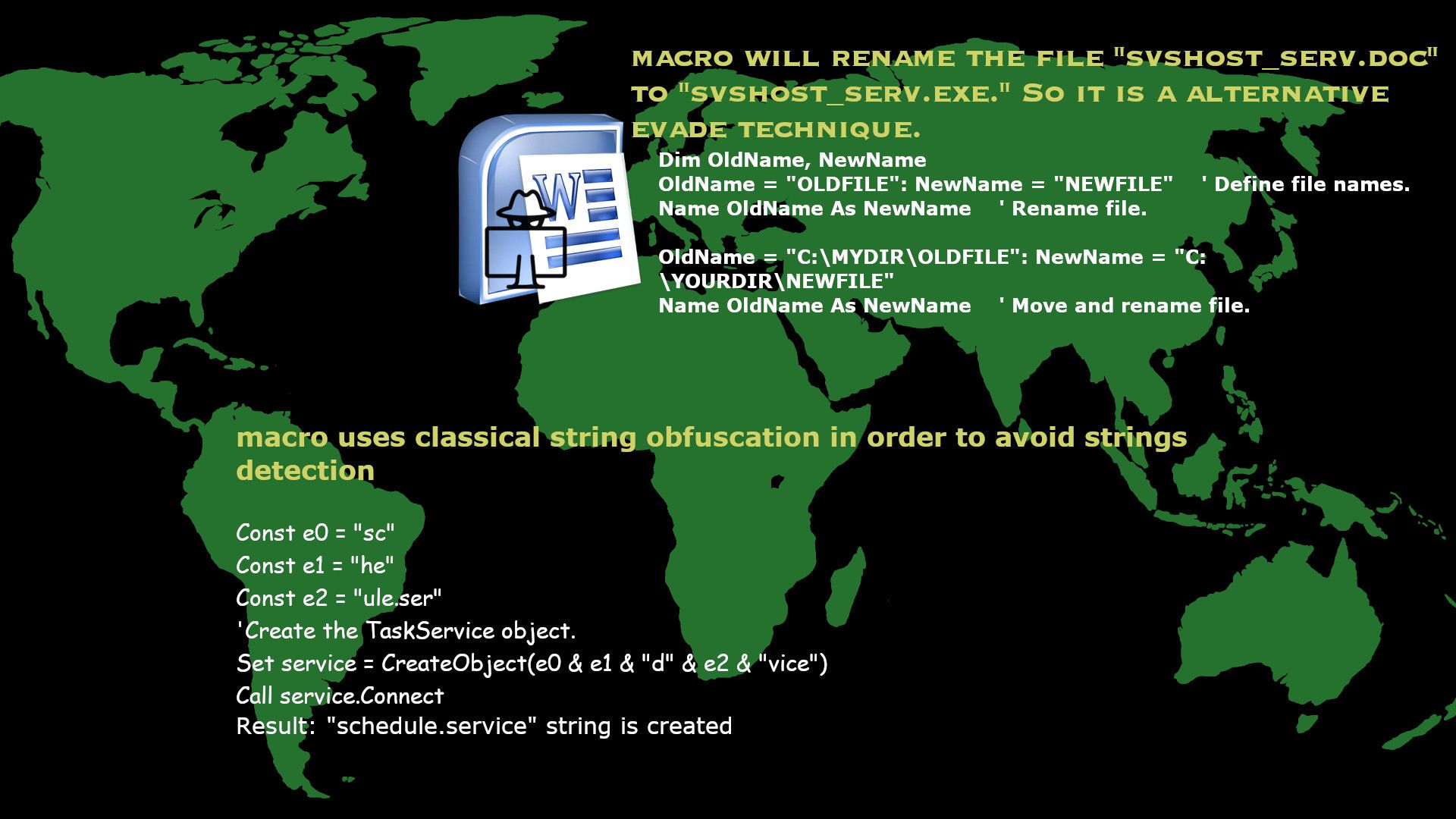
Reflection – The attack method:
Let us think that this kind of attack seems to happen in our daily lives. Perhaps sometime even though Defense mechanism not aware. Microsoft Office documents containing built-in macros is very useful and can become a Swiss army knife to hurt you. Macros are essentially bits of computer code, and historically they’ve been vehicles for malware. Should you have interest of this topic, attach diagram can provide high level overview for your reference.
Remark: Seems the SIEM endpoint event monitoring will be the effective remedy solution. However it might have involves confidential data label. So this part requires management review and separation of duties.