Preface: OPC UA is a standard that ensures the open connectivity, interoperability, security, and reliability of industrial automation devices and systems. OPC UA is widely recognized as the key communication and data modeling technology for the Industry 4.0 initiative.
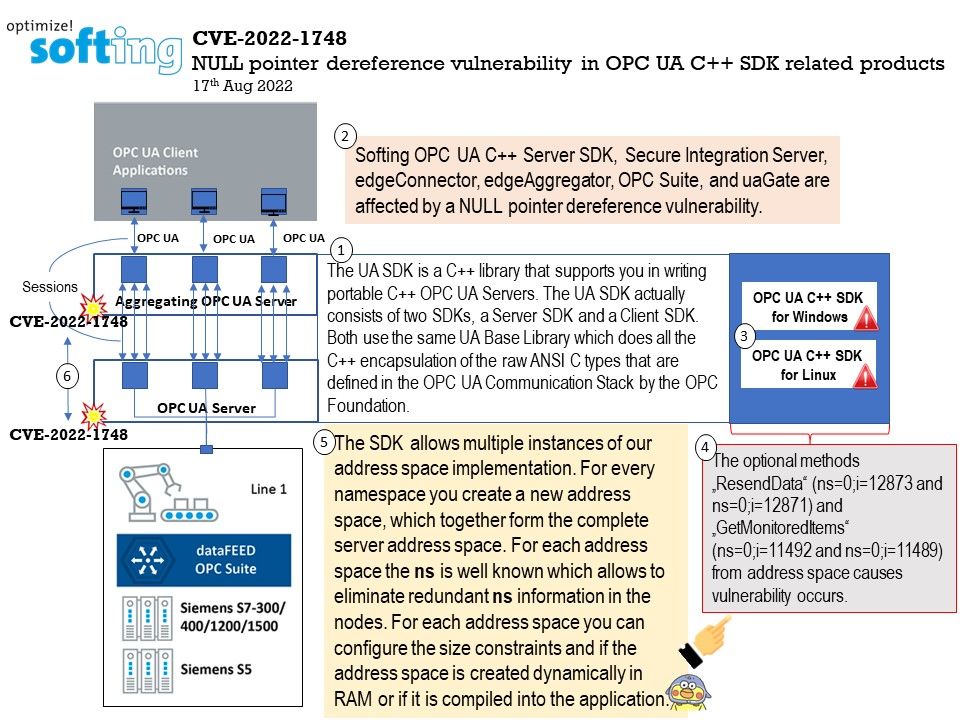
The UA SDK is a C++ library that supports you in writing portable C++ OPC UA Servers. The UA SDK actually consists of two SDKs, a Server SDK and a Client SDK. Both use the same UA Base Library which does all the C++ encapsulation of the raw ANSI C types that are defined in the OPC UA Communication Stack by the OPC Foundation.
Background: The C++ OPC UA Server SDK provides a C++ class library used to develop OPC UA Servers providing a standard interface to vendor specific systems. The OPC UA Server is normally used to describe the available information from a vendor system and to provide access to the data for external systems in a standardized way.
The SDK allows multiple instances of our address space implementation. For every namespace you create a new address space, which together form the complete server address space. For each address space the “ns” is well known which allows to eliminate redundant “ns” information in the nodes. For each address space you can configure the size constraints and if the address space is created dynamically in RAM or if it is compiled into the application.
Vulnerability details: On 17th Aug 2022, Softing OPC UA C++ SDL from version 6.0 has information update. Softing OPC UA C++ Server SDK, Secure Integration Server, edgeConnector, edgeAggregator, OPC Suite, and uaGate are affected by a NULL pointer dereference vulnerability.
NULL pointer dereference vulnerability in OPC UA C++ SDK, Secure Integration Server, edgeConnector and edgeAggregator – https://industrial.softing.com/fileadmin/psirt/downloads/syt-2022-7.html
Ref: On June 17, 2021, Softing OPC UA C++ SDK (Software Development Kit) versions from 5.59 to 5.64 exported library functions don’t properly validate received extension objects, which may allow an attacker to crash the software by sending a variety of specially crafted packets to access several unexpected memory locations.
https://nvd.nist.gov/vuln/detail/CVE-2021-32994
https://www.cisa.gov/uscert/ics/advisories/icsa-21-168-02