Preface: (BIND) is the most popular Domain Name System (DNS) server in use today. It was developed in the 1980s at the University of Berkley
and is currently in version 9.
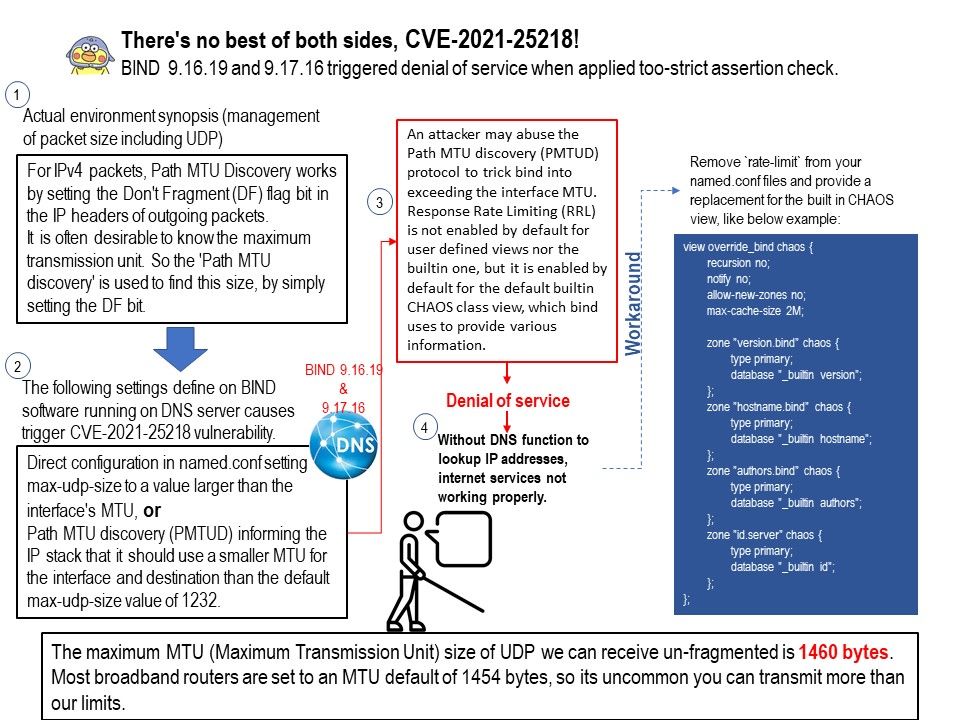
Technical Background: For IPv4 packets, Path MTU Discovery works by setting the Don’t Fragment (DF) flag bit in the IP headers of outgoing packets. Some operating systems allow packets received via other protocols to affect PMTUD values for DNS over UDP.
Set “Don’t fragment” flag in IP header:
It is often useful to avoid fragmentation, since apart from CPU utilization for fragmentation and re-assembly, it may affect throughput (if lost fragments need re-transmission). For this reason, it is often desirable to
know the maximum transmission unit. So the ‘Path MTU discovery’ is used to find this size, by simply setting the DF bit.
Vulnerability Details: An attacker may abuse the Path MTU discovery (PMTUD) protocol to trick bind into exceeding the interface MTU. Response Rate Limiting (RRL) is not enabled by default for user defined views nor the builtin one, but it is enabled by default for the default builtin CHAOS class view, which bind uses to provide various information. From technical point of view, CH class is misused by BIND!
For details of vulnerability, please refer to link – https://kb.isc.org/v1/docs/h