Preface: With Exchange Server vNext, Microsoft is phasing out the on-premise delivery model, making Exchange Server 2019 the last on-premise product version.
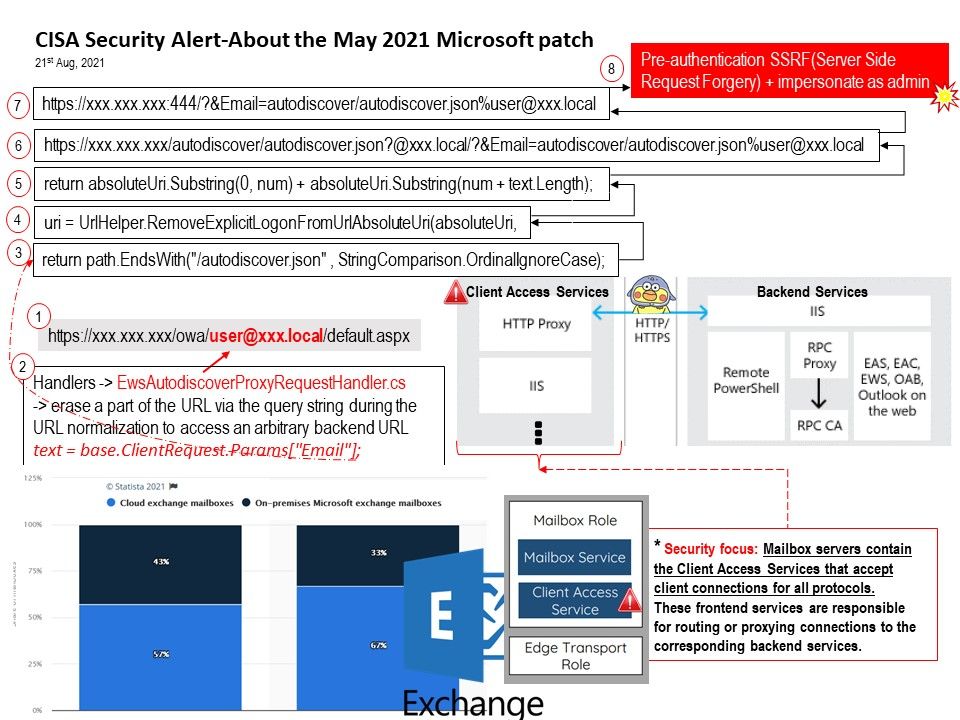
Point of view: Perhaps quite a lot of people will be surprised of this notification. Since more and more organizations has been migrated the mail server to office 365. The patch issued on May 2021 was applied already. But the patch management from small to medium firm not easy to managed. It is quite common that a one I.T. technical support person supporting everything. It is unbelievable but it is factual. You can see a lot of large size mailbox not being managed. Furthermore, the patch management may not do it immediately. It wait for their schedule time window to do the patch management. As a result, before they conduct patch management. Attacker may landed to their email server. Apart of lack of SIEM facility, only relies on a single firewall is hard to defense such vulnerability attack. Or you will say, will the local OS antivirus can be do the detection. The answer is that if the antivirus feature do not involve to content security filter function. Therefore the attack might have chance to do the evasion . I believe that CISA on their malware sink hole infrastructure will see the details. And this is the objective of this alert.
Ref: Apart from design weakness (vulnerability). The modern architecture is virtual machine infrastructure. It is not rare that the exchange server front-end and back-end are located in same hardware box because we are living in virtual machine world. So if such vulnerability occur in an on premise infrastructure. The risk will be rapidly increase.
Vulnerability details: Malicious cyber actors are actively exploiting the following ProxyShell vulnerabilities:
CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.
An attacker exploiting these vulnerabilities could execute arbitrary code on a vulnerable machine. Details can be found in the following link (CISA official announcement) – https://us-cert.cisa.gov/ncas/current-activity/2021/08/21/urgent-protect-against-active-exploitation-proxyshell