Preface: The Kalay platform contains a major vulnerability that will allow hackers to remotely access IoT devices.
Background: Kalay Platform 2.0
This newly developed decentralized structure simplifies the role of the primary server to work as an intermediary transmitter,
which reduces the chances of a server being compromised or data being intercepted. Kalay 2.0 is designed using a two-factor UID
and end-to-end encryption to support multi-factor authentication and dynamic key-pairing, the new solution ensures protection
for the end-user’s data and transmission.
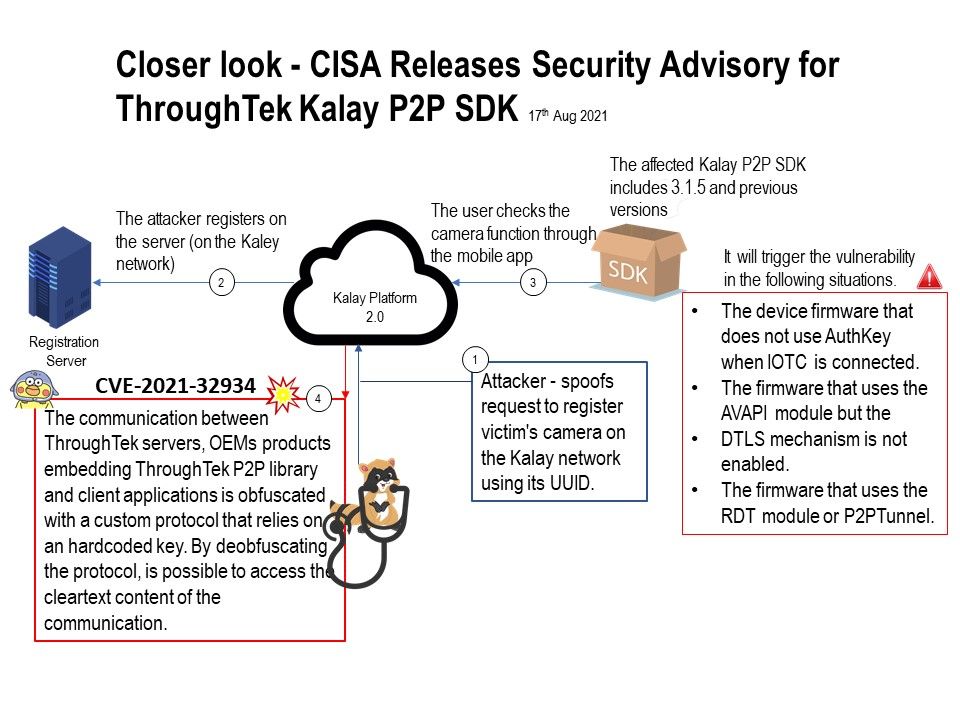
It will trigger the vulnerability in the following situations.
- The device firmware that does not use AuthKey when IOTC is connected.
- The firmware that uses the AVAPI module but the
DTLS mechanism is not enabled. - The firmware that uses the RDT module or P2PTunnel.
Basically, when vendor conducted its own security review in 2018, the vulnerability was discovered and patched, that is, the SDK version 3.1.10 released at that time has been patched.
However security consulting company “Fireye” discovered that some network surveillance cameras have security vulnerabilities, and these devices are still using the old version of TUTK SDK before 3.1.4. Therefore, the CVE-2021-32934 vulnerability was announced.
Vulnerability details:
CISA encourages users and administrators to review the ICS Advisory: https://us-cert.cisa.gov/ics/advisories/icsa-21-229-01
FireEye Mandiant blog: https://www.fireeye.com/blog/threat-research/2021/08/mandiant-discloses-critical-vulnerability-affecting-iot-devices.html