Preface: There is no limit according to the HTTP protocol itself, but implementations will have a practical upper limit. I have sent data exceeding 4 GB using POST to Apache, but some servers did have a limit of 4 GB at the time.
Background: KubeEdge consumes less resources and provides both edge-cloud collaboration and device management. So, it is suitable for internet big data center. KubeEdge is an open source system extending native containerized application orchestration and device management to hosts at the Edge. It is built upon Kubernetes and provides core infrastructure support for networking, application deployment and metadata synchronization between cloud and edge.
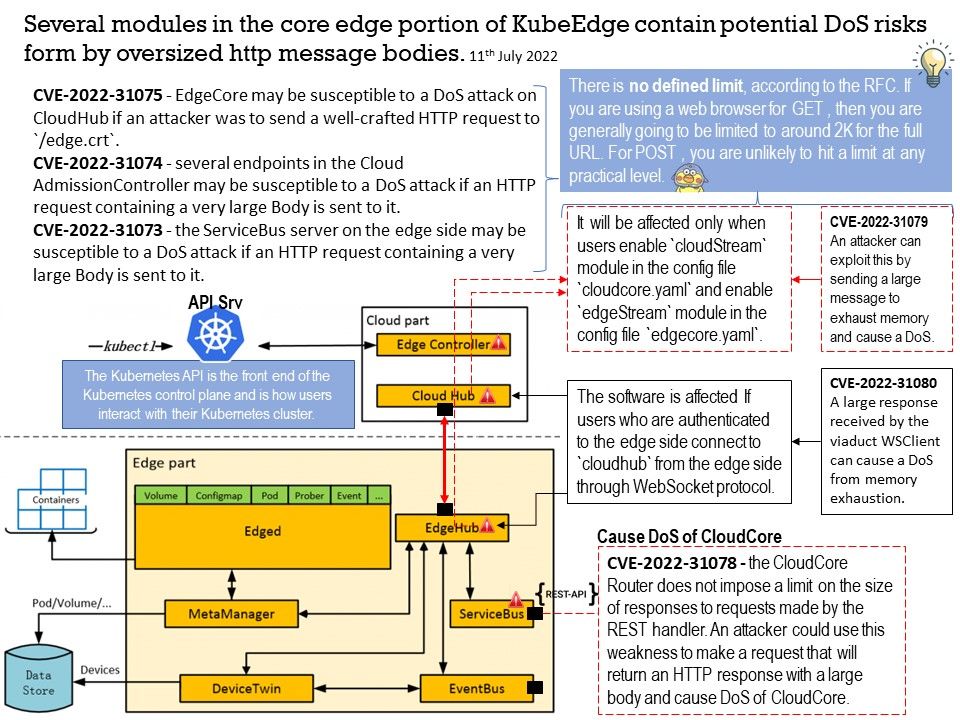
Core edge part of KubeEdge, which contains six modules: devicetwin, edged, edgehub, eventbus, metamanager, and servicebus.
Vulnerability details:
CVE-2022-31073 – the ServiceBus server on the edge side may be susceptible to a DoS attack if an HTTP request containing a very large Body is sent to it. https://github.com/kubeedge/kubeedge/security/advisories/GHSA-vwm6-qc77-v2rh
CVE-2022-31075 – EdgeCore may be susceptible to a DoS attack on CloudHub if an attacker was to send a well-crafted HTTP request to /edge[.]crt.
https://github.com/kubeedge/kubeedge/security/advisories/GHSA-x3px-2p95-f6jr
CVE-2022-31074 – several endpoints in the Cloud AdmissionController may be susceptible to a DoS attack if an HTTP request containing a very large Body is sent to it.
https://github.com/kubeedge/kubeedge/security/advisories/GHSA-w52j-3457-q9wr
CVE-2022-31078 – the CloudCore Router does not impose a limit on the size of responses to requests made by the REST handler. An attacker could use this weakness to make a request that will return an HTTP response with a large body and cause DoS of CloudCore.
https://github.com/kubeedge/kubeedge/security/advisories/GHSA-qpx3-9565-5xwm
CVE-2022-31079 – the Cloud Stream server and the Edge Stream server reads the entire message into memory without imposing a limit on the size of this message. An attacker can exploit this by sending a large message to exhaust memory and cause a DoS.
https://github.com/kubeedge/kubeedge/security/advisories/GHSA-wrcr-x4qj-j543
CVE-2022-31080 – a large response received by the viaduct WSClient can cause a DoS from memory exhaustion.
https://github.com/kubeedge/kubeedge/security/advisories/GHSA-6wvc-6pww-qr4r