Preface: The use of the custom HTTP header “SOAP Action” for SOAP web services, and cookies, and E-tags, and … well, the list goes on. HTTP headers carry data used by applications and therefore should be considered a viable transport mechanism for malicious code.
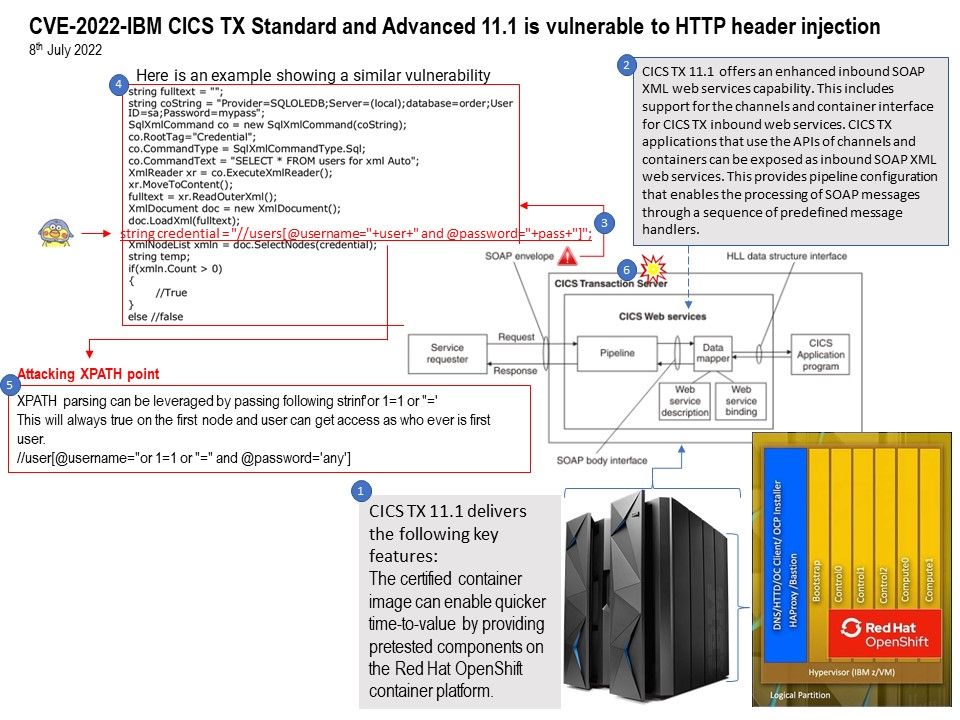
Background: CICS TX 11.1 offers an enhanced inbound SOAP XML web services capability. This includes support for the channels and container interface for CICS TX inbound web services. CICS TX applications that use the APIs of channels and containers can be exposed as inbound SOAP XML web services. This provides pipeline configuration that enables the processing of SOAP messages through a sequence of predefined message handlers.
Remark: Capability to pass more than 32K bytes of data through SOAP XML web services using channel and container APIs
Vulnerability details: IBM CICS TX Standard and Advanced 11.1 is vulnerable to HTTP header injection, caused by improper validation of input by the HOST headers. This could allow an attacker to conduct various attacks against the vulnerable system, including cross-site scripting, cache poisoning or session hijacking.
Affected Products and Versions: IBM CICS TX Advanced 11.1
Remediation: Download fix from here – https://www.ibm.com/support/fixcentral/swg/selectFixes?product=ibm%2FOther+software%2FCICS+TX+on+Cloud&fixids=ibm-cics-tx-advanced-image-11.1.0.0-ifix2&source=SAR&function=fixId&parent=ibm/Other%20software
Usage of CICS TX Standard and CICS TX Advanced (Example):
- Load a CICS TX container on Docker, open a port to connect to the container through a 3270-terminal, deploy a simple CICS COBOL application on the CICS TX container and run the application by using a 3270 terminal.
- Deploy CICS TX on a container
- Deploy CICS TX Standard on a Red Hat OpenShift Container Platform