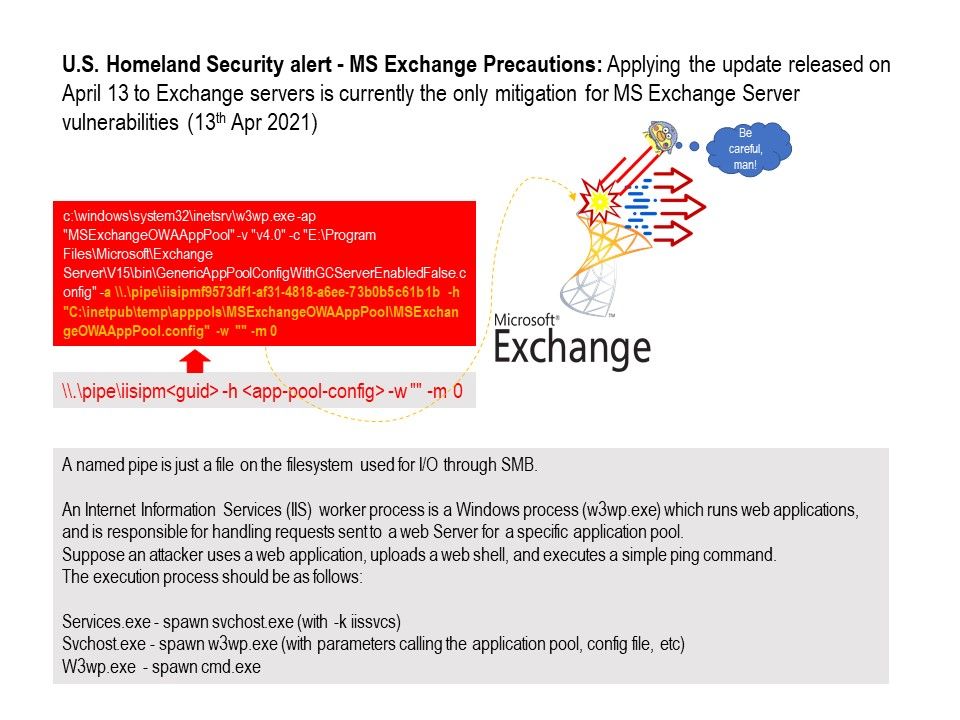
Preface: A named pipe is just a file on the filesystem used for I/O through SMB.
Background: Outlook Web App is hosted on the Client Access Server role for Exchange Server and integrated with IIS. An Internet Information Services (IIS) worker process is a Windows process (w3wp.exe) which runs web applications, and is responsible for handling requests sent to a web Server for a specific application pool. Suppose an attacker uses a web application, uploads a web shell, and executes a simple ping command.
– The execution process should be as follows:
– Services.exe – spawn svchost.exe (with -k iissvcs)
– Svchost.exe – spawn w3wp.exe (with parameters calling the application pool, config file, etc)
– W3wp.exe – spawn cmd.exe
Direction v2 – Remediation of MS exchange vulnerabilities:
On April 13, 2021, Microsoft released a software update to mitigate significant vulnerabilities that affect on-premises Exchange Servers 2013, 2016, and 2019. These vulnerabilities are different from the ones disclosed and fixed in March 2021 – the security updates released in March 2021 will not remediate against these vulnerabilities. So you should pay attention of Microsoft announcement. When patch release, it is recommend to do this patching.
Official details: https://cyber.dhs.gov/ed/21-02/#supplemental-direction-v2
Status update: Released: April 2021 Exchange Server Security Updates – https://techcommunity.microsoft.com/t5/exchange-team-blog/released-april-2021-exchange-server-security-updates/ba-p/2254617