Preface: Fileless malware can resides within volatile storage components such as memory.
About Redis: Redis is an open source (BSD licensed), in-memory data structure store, used as a database, cache and message broker. It supports data structures such as strings, hashes, lists, sets, sorted sets with range queries, bitmaps, hyperloglogs, geospatial indexes with radius queries and streams.
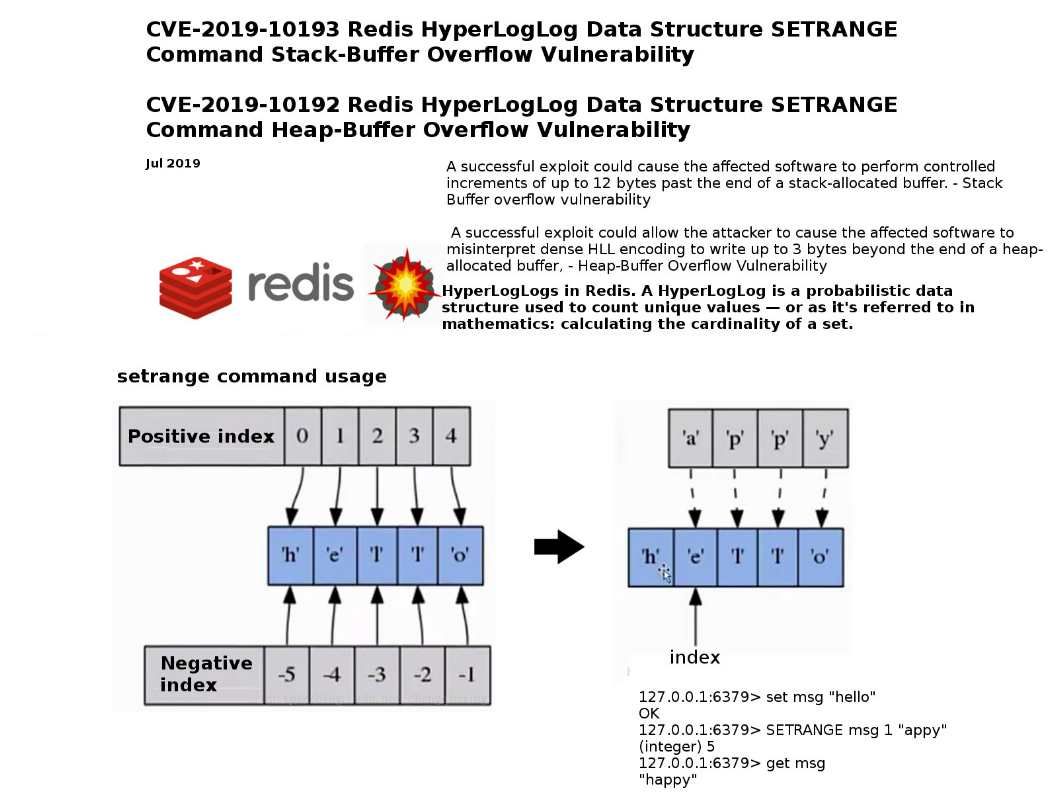
Vulnerability details: Above vulnerabilities bring our attentions because attacker could perform controlled increments of up to several bytes past the end of a stack-allocated buffer which the attacker could use to execute arbitrary code or cause a DoS condition.
Reference:
The stack is the temporary memory where variables are stored while a function is executing. The memory will be cleaned up automatically when job done.
The heap is memory that the programmer can use for the application in non automatic way. Programmer might build a mechanism to free up memory after use.
Observation: According to above details, if there are 12 bytes in the stack area which could let hacker exploit. Whereby, it will benefit to the attacker evade the defense mechanism easily.
Remedy: Redis has released software updates – http://download.redis.io/releases/