Preface: Node.js is an application runtime environment that enables using JavaScript for building server-side applications that have access to the operating system, file system, and everything else to be fully-functional. There are total 8 Top companies that rely on Node.js.
Background: Using Node.js allows organizing full stack JavaScript development ensuring the speed and performance of the application. Furthermore you are queries that how to check a process is running by the process name? Perhaps, it can use the ps-node package.
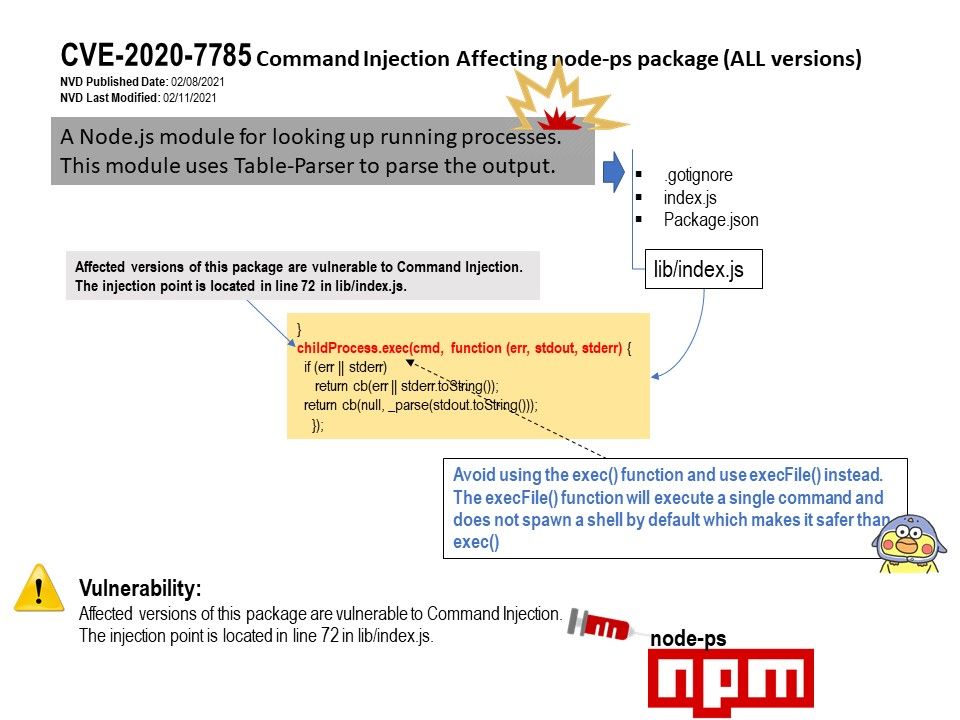
Vulnerability details: Node-ps package encountered design weakness. It found a injection point in lib/index.js. Perhaps it should avoid using the exec() function and use execFile() instead. The execFile() function will execute a single command and does not spawn a shell by default which makes it safer than exec().
Remark: By default, pipes for stdin, stdout, and stderr are established between the parent Node.js process and the spawned subprocess.
Official announcement: https://nvd.nist.gov/vuln/detail/CVE-2020-7785