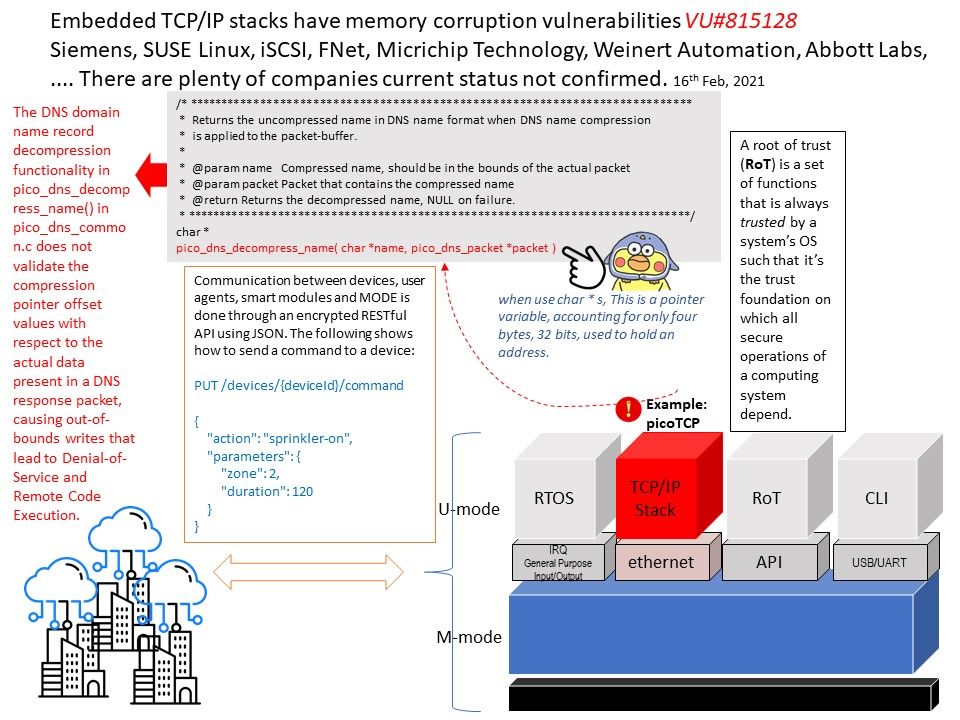
Preface: Embedded TCP/IP stacks have memory corruption vulnerabilities (Vulnerability Note VU#815128) – Siemens, SUSE Linux, iSCSI, FNet, Micrichip Technology, Weinert Automation, Abbott Labs, ….
There are plenty of companies current status not confirmed.
Background: CERT Coordination Center alert to public on December 2020 that the TCP/IP stacks has memory corruption vulnerabilities. Therefore, this design weakness is impacting the IoT world. Forescout Research Labs discovered 33 vulnerabilities impacting millions of IoT, OT and IT devices that present an immediate risk for organizations worldwide. So called amnesia33. A closer look of vulnerability checklist, you will find that there are plenty of vulnerabilities result deny of service & info leak. Furthermore, CVE-2020-24336 & CVE-2020-24338 flaw will allow attacker to do a remote code execution (RCE).
Security focus: The serious impact is RCE caused by defects in the DNS function shown on report issued by Forescout. The flaw shown that the processes DNS queries and responses has plenty of issues. Refer below:
- no check on whether a domain name is nukk-terminated.
- DNS response data length is not checked
- DNS queries and response (set in DNS header) is not checked against the data present
- length byte of a domain name in a DNS query and response is not checked and is used for internal
memory operations.
Current status: We are still waiting for vendor response. For detail, please refer to link – https://kb.cert.org/vuls/id/815128