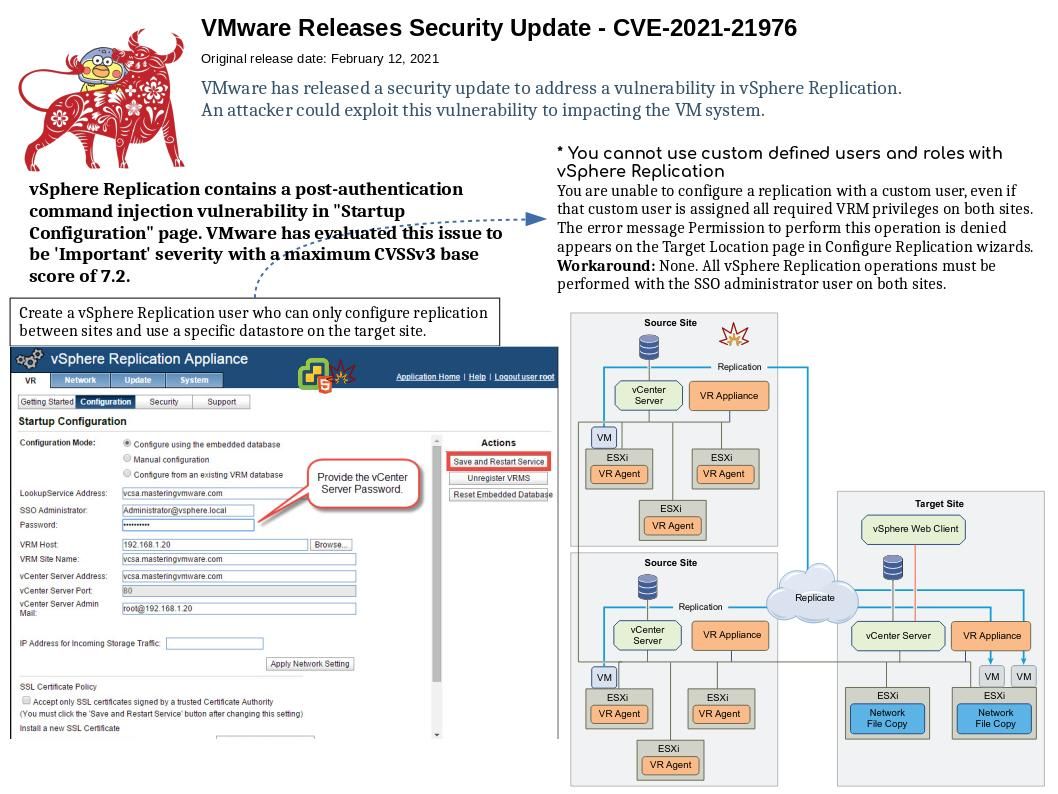
Preface: With vSphere Replication, you can set up replication of VM from the source site to the target site, monitor and manage the replication status, and restore VM on the target site.
Background: vSphere Replication is an alternative to storage-based replication. It protects virtual machines from partial or complete site failures by replicating the virtual machines from a source site to a target site. Some configuration files contain settings that affect the security of vSphere Replication (see below):
– The default system configuration of the vSphere Replication Management server.
[/]opt[/]vmware[/]hms[/]conf[/]hms-configuration.xml
– The configuration file for the embedded database.
[/]opt[/]vmware[/]hms[/]conf[/]embedded_db.cfg
Vulnerability details: Attacker with administrative access in vSphere Replication can execute shell commands on the underlying system. Successful exploitation of this issue may allow authenticated admin user to perform a remote code execution.
Official announcement: https://www.vmware.com/security/advisories/VMSA-2021-0001.html
Remark: If html page lack of sanitization function and causes the injection of command. The impact may unforeseeable.