Preface: Security Alert from the vendor (Apple) on 17th Aug 2022, found a bug on their iOS. If you use iPhone and iPad, you need to update now. Some experts said that the update was also taken seriously by security research unit ZecOps, who tweeted that the iOS 15.6.1 patch vulnerability was already in use, and emphasized that hackers may launch one-click and “zero-click attacks”. Same strategy as NSO Group Pegasus Spyware.
What is zero-click attack?
On 2021, cybersecurity firm ZecOps claimed iPhones and iPads have had a traditional vulnerability to unassisted attacks, especially with its mail app. From iOS 13, this became a vulnerability to zero-click attacks too. “The vulnerability allows remote code execution capabilities and enables an attacker to remotely infect a device by sending emails that consume a significant amount of memory,” a ZecOps blog published this April said. Apple reportedly patched this in April 2020.
Background: The vulnerability has been fixed, why is there another round of attacks on iPhones and iPads around the world?
As we know, the Linux kernel is composed of multiple kernel types, whereas the iOS kernel types use hybrids.
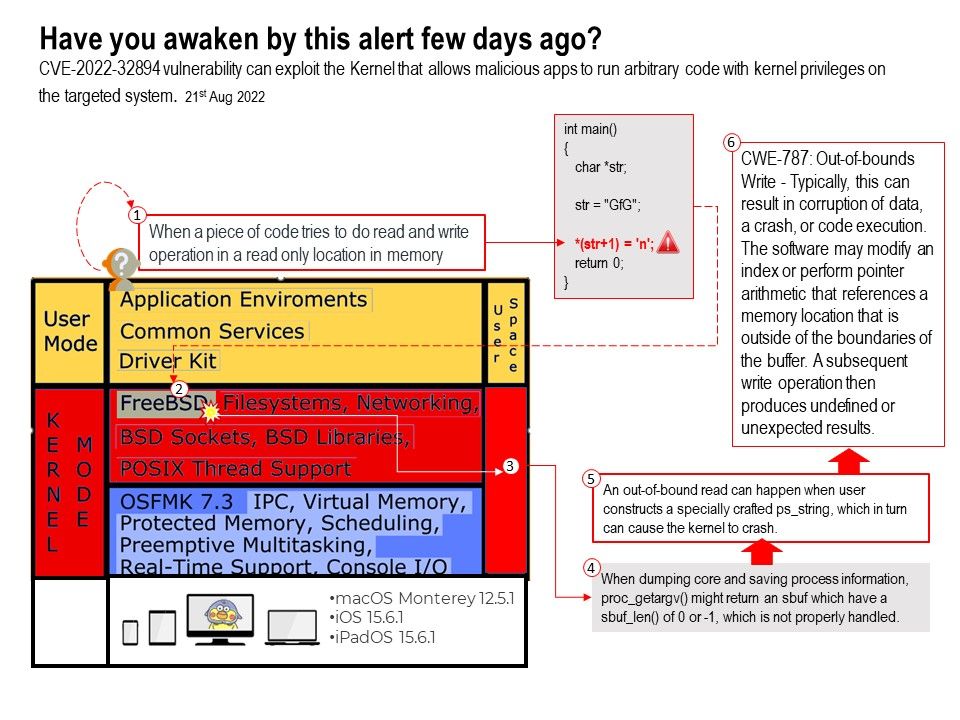
Since the CVE vulnerability information stated that this vulnerability is caused by an out-of-bounds vulnerability. The vendor, as usual, did not disclose details. But which key point drives the vendor to issue a remedy immediately? Let’s imagine the flaw based on the hints provided. In a multi-core environment, it is possible to trigger similar attacks. The attached image is when multiple kernels encounter errors on FreeBSD. For example, the vulnerability for FreeBSD was released on August 10, 2022. The vulnerability is an out-of-bounds read in elf_note_prpsinfo(). According to this circumstances, when an operating system runs on a multi-kernel system architecture (includes the FreeBSD operating system architecture). An out-of-scope defect occurred by design weakness.Thus triggering a serious flaw.
Above is only an example, as a matter of fact not know what the vulnerability was? But even what is the root causes , nobody can tell?
But if you keep your eyes open, when there is a new unknown critical bug occurs in on going future.
CWE-787: Out-of-bounds Write – Typically, this can result in corruption of data, a crash, or code execution. The software may modify an index or perform pointer arithmetic that references a memory location that is outside of the boundaries of the buffer. A subsequent write operation then produces undefined or unexpected results.
Remark: The Service.RestartSec setting specifies the downtime in seconds after which systemd restarts a crashed service (5 seconds by default).
Vulnerability details:
CVE-2022-32893 vulnerability can exploit the WebKit that allows crafted web content to run arbitrary code on the targeted system.
CVE-2022-32894 vulnerability can exploit the Kernel that allows malicious apps to run arbitrary code with kernel privileges on the targeted system.
Fixes and Solutions:
Safari 15.6.1 | HT213414 – https://support.apple.com/en-gb/HT213414
macOS Monterey 12.5.1 | HT213413 – https://support.apple.com/kb/HT213413
iOS 15.6.1 and iPadOS 15.6.1 | HT213412 – https://support.apple.com/kb/HT213412