Preface: OPC UA bridges the divide between information technology and operational technology. It enables information and data exchange on devices within machines, between machines, and from machines to systems. As a result, companies cannot realize the benefits of the Internet of Things (IoT) and Industry 4.0 without OPC UA.
Background: Microsoft contributing Open-Source OPC UA stack to OPC Foundation on 2017. Upon today, the new OPC Foundation .NET reference stack, based on the new .NET Standard Library technology, was developed and optimized by Microsoft to serve as the complete platform-independent infrastructure, from the embedded world to the cloud.
This new version is enabled on the following supported platforms: Various Linux distributions, iOS, Android, Windows 7, Windows 8, Windows 8.1, Windows 10, Windows Phone, HoloLens and the Azure cloud.
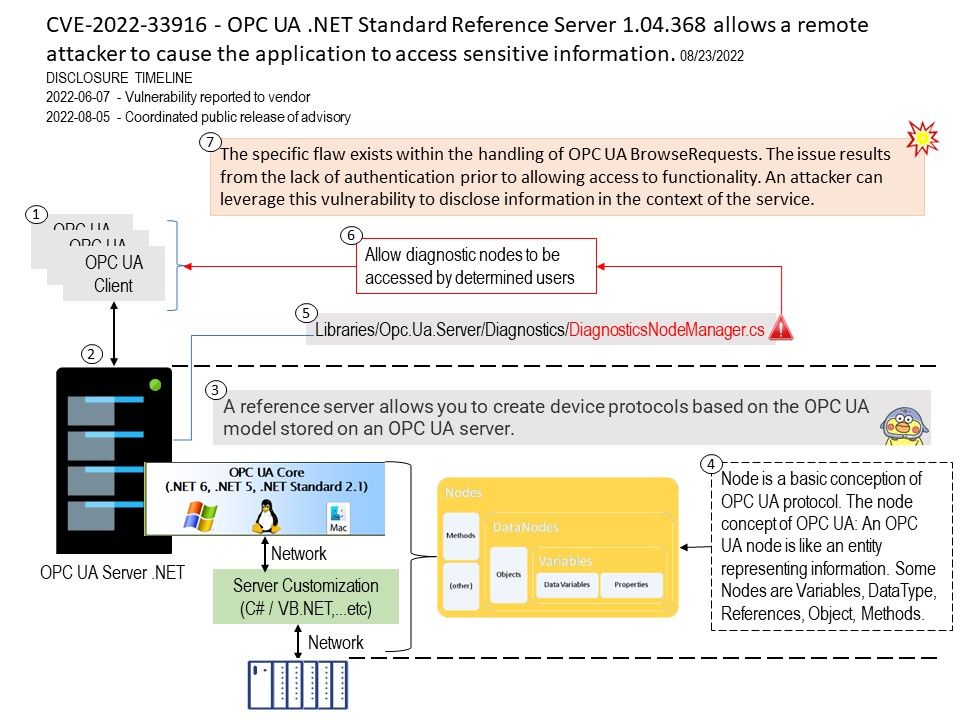
Vulnerability details: The vulnerability exists due to excessive data output by the application within the handling of OPC UA BrowseRequests. A remote attacker can gain unauthorized access to sensitive information on the system.
With the information obtained an unauthorized user can create a valid session with the OPC UA server or client to obtain sensitive information.
OPC Foundation Security Bulletin – https://files.opcfoundation.org/SecurityBulletins/OPC%20Foundation%20Security%20Bulletin%20CVE-2022-33916.pdf