Preface: User Account Control (UAC) is a fundamental component of Microsoft’s overall security vision. UAC helps mitigate the impact of malware.
Synopsis: UAC Bypass Using eventvwr.exe was exploited by malware in 2017. Microsoft fixes Eventvwr.exe UAC Bypass Exploit in Windows 10 Creators Update. In Windows 10 Creators Update preview build 15007, Microsoft seems to have fixed the UAC bypass method involving eventvwr.exe. But the investigator still discovered similar of UAC bypass exploit technique was used by ransomware.
In April of 2019, expert found a new type of ransomware named Sodinokibi. Their design utilize a module loaded into memory functions as a loader on phase 1. Meanwhile it will try to conduct UAC bypass if the processes privileges are insufficient.
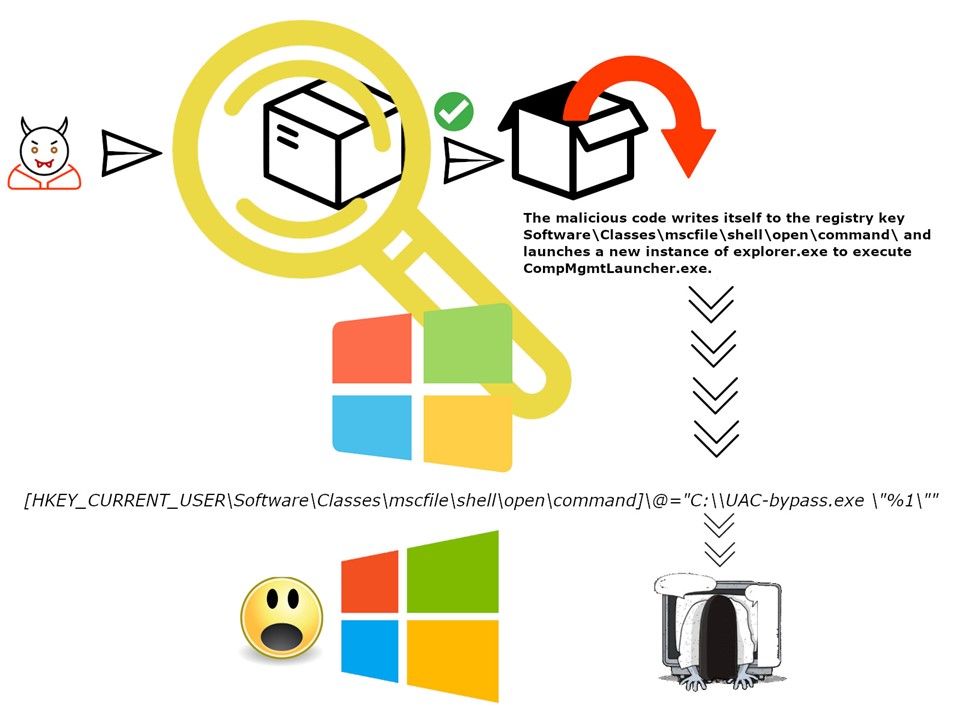
The mechanism of UAC bypass technique not limit to use eventvwr.exe. The attacker can writes itself to the registry key (Software\Classes\mscfile\shell\open\command) and launches a new instance of explorer.exe to execute compmgmtlauncher.exe. Whereby it executes anything configured in the registry key Software\Classes\mscfile\shell\open\command\ then execute a script (see above diagram).
So, we have a basic concept that if we only following vendor announcement conduct a patch management will not be a efficient technique to protect your machine avoid ransomware attack.
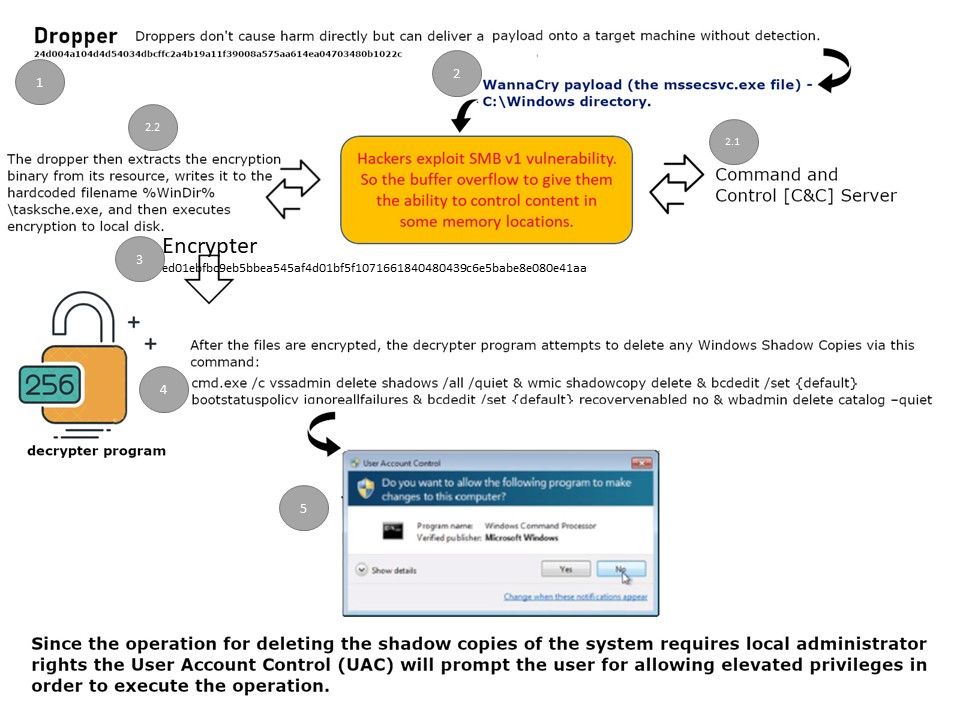
Objectives and definitions for establishing light weapons: In order to avoid the detection of the anti-malware mechanism, quite a lot of notorious APT malware will be relied on design weakness of UAC. As a result, it can bypass the access control, meanwhile it can significant increase the successful rate of the phase one of cyber attack because it bring the difficulties to the defense mechanism. The fact is that only detect a simple script or code not easy to predict what the intention was. When Wannacry ransomware was born, perhaps the design goal is SMB vulnerability. But it lack of competence of the attack strategy. Whereby, when ransomware take the action to deleting the shadow copies of the system requires local administrator rights the User Account Control will prompt the user for allowing elevated privileges in order to execute the operation (see below diagram). So it alert the end user something will be happened when it click. Therefore the new generation of ransomware try to management this design weakness.
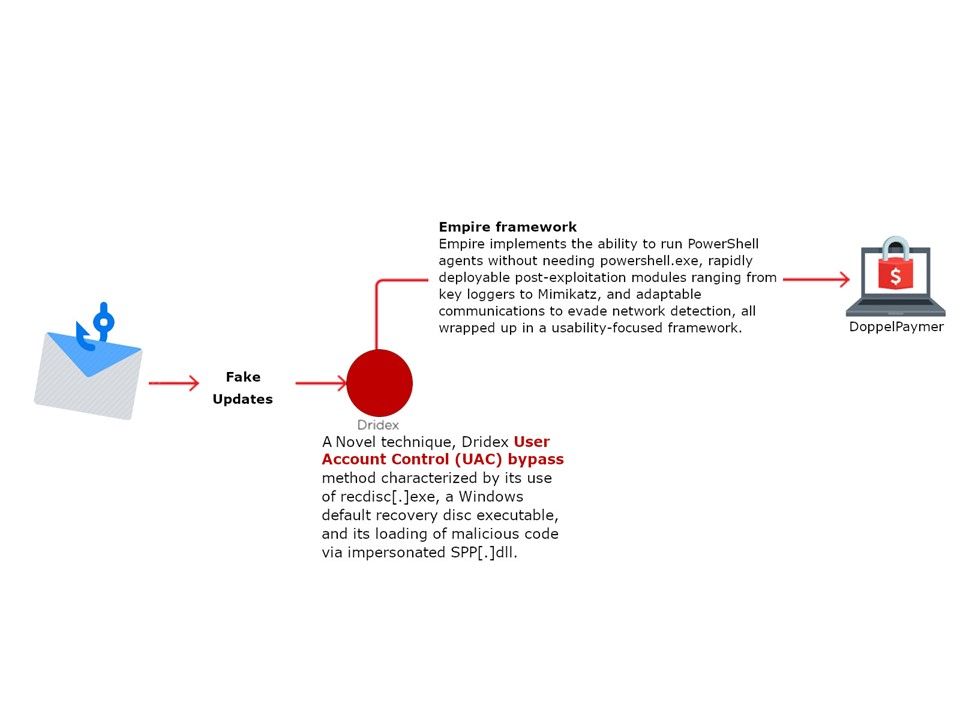
Ransomware author leverage UAC Bypass technique: A novel technique, Dridex User Account Control (UAC) bypass method characterized by its use of recdisc[.]exe, a Windows default recovery disc executable, and its loading of malicious code via impersonated SPP[.]dll. Perhaps you might say, this vulnerability has been fixed by Microsoft. But the market feedback is as follow:
Microsoft doesn’t consider UAC a security barrier, and thus they often don’t fix UAC bypasses. These bypasses are common and easy. The following figure shows another scenario of UAC bypass.
Let’s open our eyes and see what happens in the evolving world of cybersecurity?
……………………………………………..END
Additional topic: I am wishing that the Coronavirus will be gone in next morning. Perhaps it was not possible but such punishment to man kind that has been enough!