Preface: CarrierWave provides a simple and extremely flexible way to upload files from Ruby applications. Ruby On Rails Companies Websites are popular. It covered all your familiar areas – Airbnb, Groupon, GitHub, Twitter, Zendesk, Bloomberg…
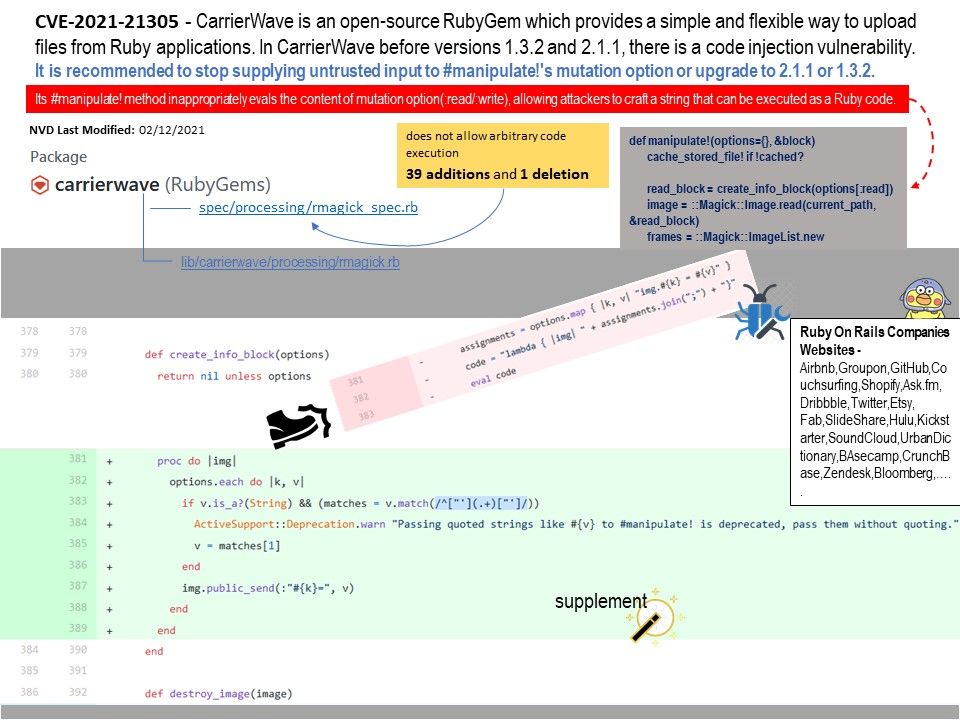
Background: CarrierWave is an open-source RubyGem which provides a simple and flexible way to upload files from Ruby applications. In CarrierWave before versions 1.3.2 and 2.1.1, there is a code injection vulnerability.
Vulnerability details: The “#manipulate!” method inappropriately evals the content of mutation option(:read/:write), allowing attackers to craft a string that can be executed as a Ruby code. If an application developer supplies untrusted inputs to the option, it will lead to remote code execution(RCE). For more details, please refer to diagram.
Workaround: It is recommended to stop supplying untrusted input to #manipulate!’s mutation option.
Remedy: upgrade to 2.1.1 or 1.3.2.
Reference: RubyGems is a package manager for Ruby. It provides a standard format “gem” for distributing Ruby programs and libraries. It is designed to conveniently manage gem installation tools and servers for distributing gems. This is similar to Python’s pip.