Preface: KVM hypervisor enables full virtualisation capabilities. It provides each VM with all typical services of the physical system, including virtual BIOS (basic input/output system) and virtual hardware, such as processor, memory, storage, network cards, etc. As a result, every VM completely simulates a physical machine.
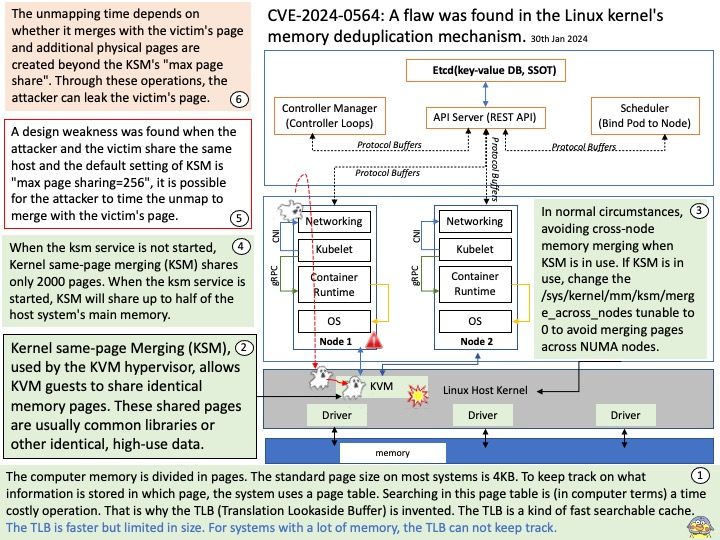
Background: Kernel same-page Merging (KSM), used by the KVM hypervisor, allows KVM guests to share identical memory pages. These shared pages are usually common libraries or other identical, high-use data. KSM allows for greater guest density of identical or similar guest operating systems by avoiding memory duplication.
Vulnerability details: A flaw was found in the Linux kernel’s memory deduplication mechanism. The max page sharing of Kernel Samepage Merging (KSM), added in Linux kernel version 4.4.0-96.119, can create a side channel. When the attacker and the victim share the same host and the default setting of KSM is “max page sharing=256”, it is possible for the attacker to time the unmap to merge with the victim’s page. The unmapping time depends on whether it merges with the victim’s page and additional physical pages are created beyond the KSM’s “max page share”. Through these operations, the attacker can leak the victim’s page.
Ref: It leaves one page unchanged, and re-maps each duplicate page to point to the same physical page, after which it releases the extra physical pages for re-use.
Mitigation: Deactivating memory deduplication will effectively mitigate all attack vectors. This measure unfortunately eliminates all the highly appreciated benefits of memory deduplication, namely the increase of operational cost-effectiveness through inter-VM memory sharing. This will cause an increase in the amount of memory required and in some situations may adversely impact performance (e.g. due to slower swap space being used). It is recommended that customers test this workaround before using it in production. See https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/virtualization_tuning_and_optimization_guide/sect-ksm-deactivating_ksm for how to disable KSM from Red Hat Enterprise Linux 6 and newer.
Official details: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-0564