Preface: MobileIron was acquired by Ivanti on December 1, 2020. Ivanti acquired Pulse Secure that same year. As part of the acquisition, Pulse Secure has been renamed Ivanti Secure Access. Starting October 9, 2023, Pulse Secure/Ivanti Secure Access will be upgraded to the latest version of Ivanti Secure Access.
Background: Ivanti Connect Secure (ICS) provides secure connection. Ivanti Connect Secure includes VPN deployments and simplified appliance management. Ivanti Policy Secure (IPS) is a network access control (NAC) solution which provides network access only to authorized and secured users and devices.
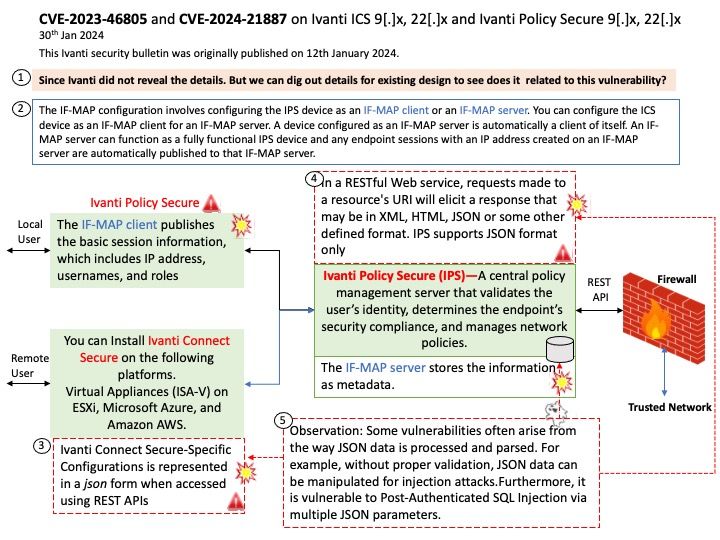
The REST API provides a standardized method for Next-Gen firewalls and third-party systems to interact with IPS. Representational state transfer (REST) or RESTful Web services are one way of providing interoperability between computer systems on the Internet. In a RESTful Web service, requests made to a resource’s URI will elicit a response that may be in XML, HTML, JSON or some other defined format. IPS supports JSONformat only.
Vulnerability details:
CVE-2023-46805: An authentication bypass vulnerability in the web component of Ivanti ICS 9.x, 22.x and Ivanti Policy Secure allows a remote attacker to access restricted resources by bypassing control checks.
CVE-2024-21887: A command injection vulnerability in web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) allows an authenticated administrator to send specially crafted requests and execute arbitrary commands on the appliance.
My observation: Some vulnerabilities often arise from the way JSON data is processed and parsed. For example, without proper validation, JSON data can be manipulated for injection attacks. Furthermore, it is vulnerable to Post-Authenticated SQL Injection via multiple JSON parameters.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-46805