Preface: Use after free errors sometimes have no effect and other times cause a program to crash. While it is technically feasible for the freed memory to be re-allocated and for an attacker to use this reallocation to launch a buffer overflow attack.
Background: Systems with Mali GPUs typically have a shared memory, so you are not required to copy data. This parameter CL_MEM_ALLOC_HOST_PTR is the best way to avoid a copy.
This is a hint to the driver indicating that the buffer is accessed on the host side. To use the buffer on the application processor side, you must map this buffer and write the data into it. This is the only method that does not involve copying data. If you must fill in an image that is processed by the GPU. This is the best way to avoid copy.
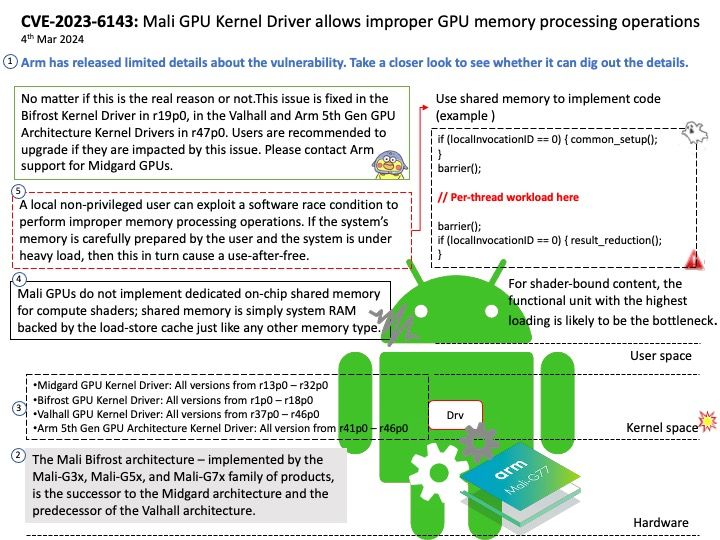
Vulnerability details: A local non-privileged user can exploit a software race condition to perform improper memory processing operations. If the system’s memory is carefully prepared by the user and the system is under heavy load, then this in turn cause a use-after-free.
Resolution: This issue is fixed in the Bifrost Kernel Driver in r19p0, in the Valhall and Arm 5th Gen GPU Architecture Kernel Drivers in r47p0. Users are recommended to upgrade if they are impacted by this issue. Please contact Arm support for Midgard GPUs.
Official announcement: Please refer to the link for details – https://developer.arm.com/Arm%20Security%20Center/Mali%20GPU%20Driver%20Vulnerabilities