Preface:An essential race condition occurs when an input has two transitions in less than the total feedback propagation time.
Background: ICMPv6 over the Internet is important for Path MTU Discovery (which uses the ICMPv6 Packet Too Big message) since ipv6 routers don’t fragment packets. ICMPv6 is an integral part of IPv6 and performs error reporting and diagnostic functions.
ICMP in IPv6 functions the same as ICMP in IPv4. ICMP for IPv6 generates error messages, such as ICMP destination unreachable messages, and informational messages, such as ICMP echo request and reply messages.
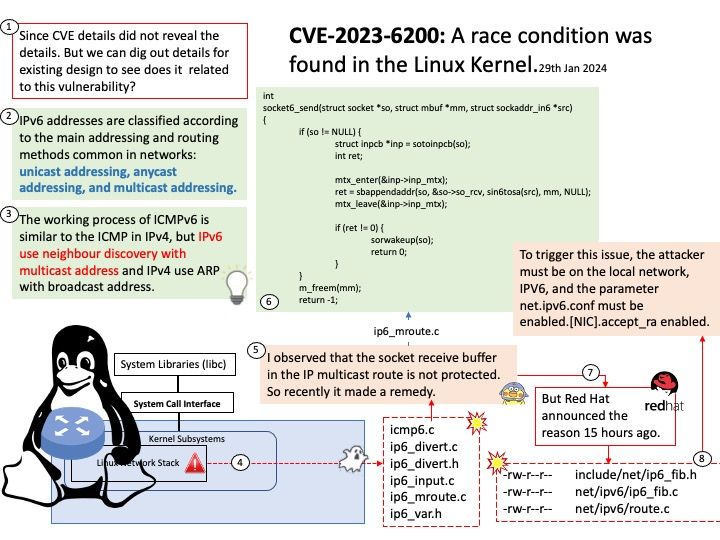
The working process of ICMPv6 is similar to the ICMP in IPv4, but IPv6 use neighbor discovery with multicast address and IPv4 use ARP with broadcast address.
Vulnerability details: A race condition was found in the Linux Kernel. Under certain conditions, an unauthenticated attacker from an adjacent network could send an ICMPv6 router advertisement packet, causing arbitrary code execution.
Workaround suggested by Red Hat: To trigger this issue, the attacker must be on the local network, IPV6, and the parameter net.ipv6.conf must be enabled.[NIC].accept_ra enabled. By default, net.ipv6.conf.[NIC].accept_ra is disabled for Red Hat Enterprise Linux. In the default configuration, only local attacks are possible.
Official announcement: Please refer to the link for details – https://access.redhat.com/security/cve/cve-2023-6200