Preface: The Unbreakable Enterprise Kernel (UEK) is a Linux kernel built by Oracle and supported through Oracle Linux support. Reliable Datagram Sockets (RDS) is a high-performance, low-latency, reliable, connectionless protocol for delivering datagrams. It is developed by Oracle Corporation. It was included in the Linux kernel 2.6.30 which was released on 9th of June, 2009.
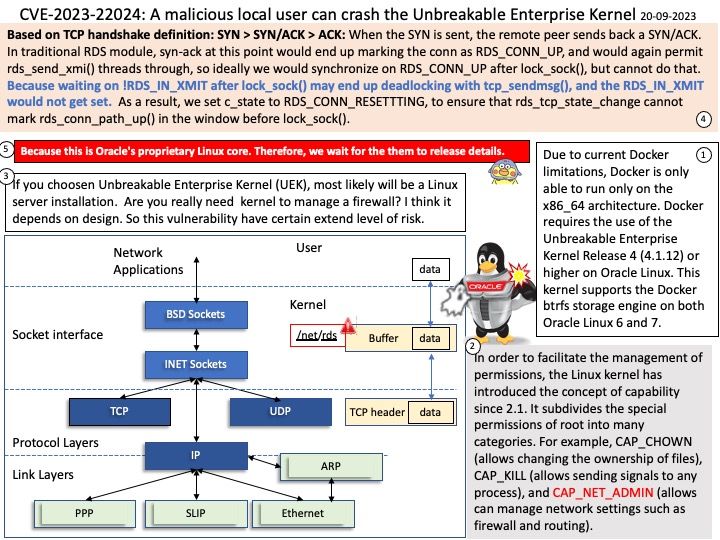
Background: Based on TCP handshake definition: SYN > SYN/ACK > ACK: When the SYN is sent, the remote peer sends back a SYN/ACK. In traditional RDS module, syn-ack at this point would end up marking the conn as RDS_CONN_UP, and would again permit rds_send_xmi() threads through, so ideally we would synchronize on RDS_CONN_UP after lock_sock(), but cannot do that.
Because waiting on !RDS_IN_XMIT after lock_sock() may end up deadlocking with tcp_sendmsg(), and the RDS_IN_XMIT would not get set.
As a result, we set c_state to RDS_CONN_RESETTTING, to ensure that rds_tcp_state_change cannot mark rds_conn_path_up() in the window before lock_sock().
Vulnerability details: In the Unbreakable Enterprise Kernel (UEK), the RDS module in UEK has two setsockopt(2) options, RDS_CONN_RESET and RDS6_CONN_RESET, that are not re-entrant. A malicious local user with CAP_NET_ADMIN can use this to crash the kernel.
CVSS 3.1 Base Score 5.5
Official announcement: For details,please refer to the link – https://linux.oracle.com/cve/CVE-2023-22024.html