Preface: A Subject Alternate Name (or SAN) certificate is a digital security certificate which allows multiple hostnames to be protected by a single certificate. A SAN certificate may also be called a Unified Communication Certificate (or UCC), a multi-domain certificate, or an Exchange certificate.
A Subject Alternative Name (SAN) certificate is capable of supporting multiple domains and multiple host names with domains. SANS certificates are more flexible than Wildcard certificates since they are not limited to a single domain.
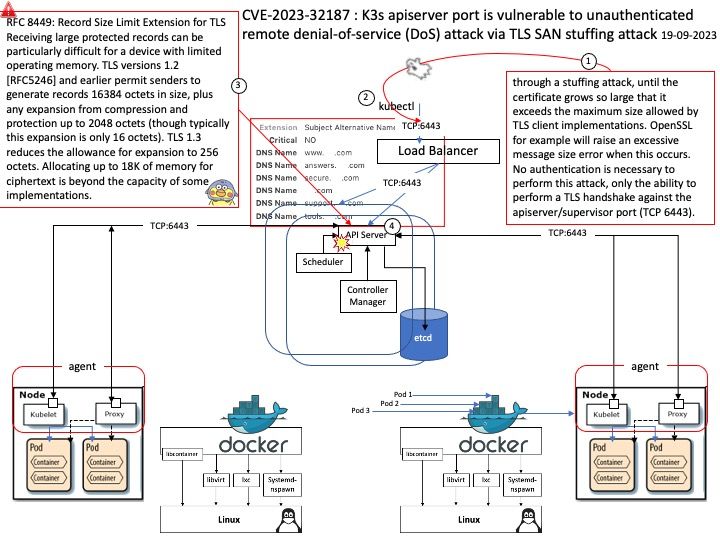
Vulnerability Description: An Allocation of Resources Without Limits or Throttling vulnerability in SUSE k3s allows attackers with access to K3s servers’ apiserver/supervisor port (TCP 6443) cause denial of service. This issue affects k3s: from v1.24.0 before v1.24.17+k3s1, from v1.25.0 before v1.25.13+k3s1, from v1.26.0 before v1.26.8+k3s1, from sev1.27.0 before v1.27.5+k3s1, from v1.28.0 before v1.28.1+k3s1.
Ref: An issue was found in K3s where an attacker with network access to K3s servers’ apiserver/supervisor port (TCP 6443) can force the TLS server to add entries to the certificate’s Subject Alternative Name (SAN) list, through a stuffing attack, until the certificate grows so large that it exceeds the maximum size allowed by TLS client implementations. OpenSSL for example will raise an excessive message size error when this occurs. No authentication is necessary to perform this attack, only the ability to perform a TLS handshake against the apiserver/supervisor port (TCP 6443).
Upstream Security Advisories:
https://github.com/k3s-io/k3s/security/advisories/GHSA-m4hf-6vgr-75r2
SUSE information
Overall state of this security issue: Analysis
This issue is currently rated as having important severity.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-32187