Preface: Perhaps this isn’t the first time this year we’ve heard of Safari and iOS having design flaws. Since both elements are close to each other. It is inevitable that it may have an impact. In addition, Safari includes open source code. So when a design flaw is discovered, sometimes the results look similar. The reason is that it happens in the same component, but that component is composed of other open source software.
In accordance with Apple’s Vulnerability Management Policy. Due to commercial reasons, technical details are not disclosed. But if anyone is interested in what happened. Increases the difficulty of analysis. But no harm. Bold assumptions and careful verification are the definition of science.
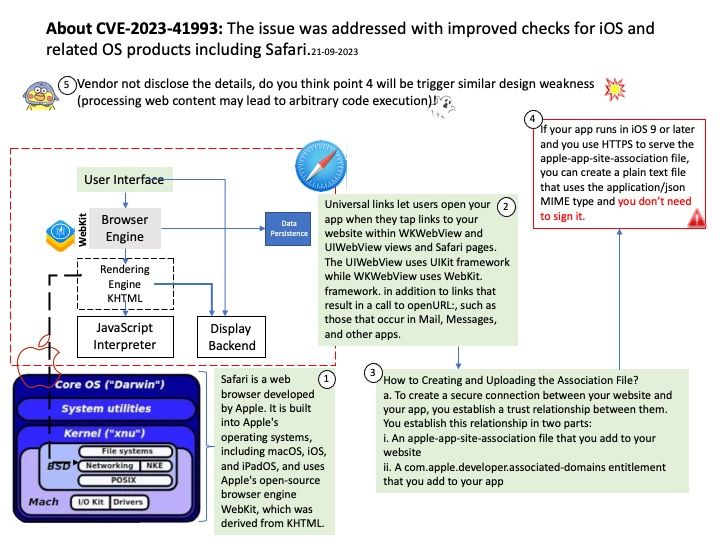
Background: On iOS and related software operating system products (macOS and iPadOS), Safari is built into the operating system (OS). Furthermore, it uses Apple’s open source browser engine WebKit, which is derived from KHTML. WebKit is a browser engine developed by Apple and primarily used in its Safari web browser, as well as all web browsers on iOS and iPadOS. Removing Safari is not recommended as it may damage the operating system and cause your Apple device to malfunction. Technically, If you don’t use Safari, it doesn’t accumulate caches or other service files.
Vulnerability details: The issue was addressed with improved checks. This issue is fixed in Safari 16.6.1, macOS Ventura 13.6, OS 17.0.1 and iPadOS 17.0.1, iOS 16.7 and iPadOS 16.7. Processing web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.7.
My observation: Vendor not disclose the details, do you think point b will be trigger similar design weakness (processing web content may lead to arbitrary code execution)!
Universal links let users open your app when they tap links to your website within WKWebView and UIWebView views and Safari pages. The UIWebView uses UIKit framework while WKWebView uses WebKit. framework. in addition to links that result in a call to openURL:, such as those that occur in Mail, Messages, and other apps.
How to Creating and Uploading the Association File?
a.To create a secure connection between your website and your app, you establish a trust relationship between them. You establish this relationship in two parts:
i.An apple-app-site-association file that you add to your website
ii.A com.apple.developer.associated-domains entitlement that you add to your app
b.If your app runs in iOS 9 or later and you use HTTPS to serve the apple-app-site-association file, you can create a plain text file that uses the application/json MIME type and you don’t need to sign it.
Official announcement: Please refer to the following link for details –