Preface: If you were a child, you would think of the moon and Mars. Furthermore you will think about robot and extraterrestrial. But you might not think about design weakness, so called vulnerability.
Background: Robot Operating System (ROS) is a set of open source algorithms, hardware driver software and tools developed to develop robot control software. Despite having an operating system in its name, it is not an operating system.
- Communication System (Publish Subscribe and Remote Method Invocation),
- Framework & Tools (Build system & dependency management, Visualization, Record and Replay)
- Ecosystem (Language bindings, Drivers, libraries and simulation (Gazebo)).
Distributed applications are designed as units called nodes. In robotic systems, sensors (lidars, cameras) motion controllers (motors that provide motion), and algorithmic components (route planners) can all be nodes. ROS 2 separates the node concept from the OS-level process structure.
All nodes in the system can be run on a single computer or they can be distributed and run across multiple computers.
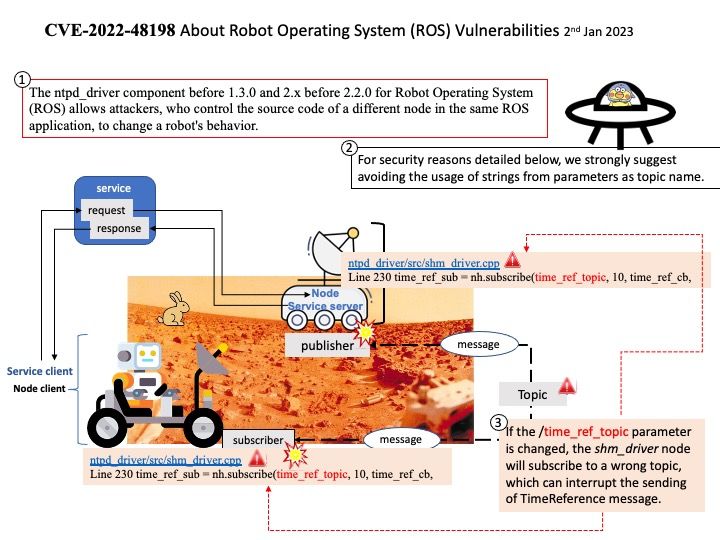
Vulnerability details: The ntpd_driver component before 1.3.0 and 2.x before 2.2.0 for Robot Operating System (ROS) allows attackers, who control the source code of a different node in the same ROS application, to change a robot’s behavior.
Official announcement: For details, see the link – https://nvd.nist.gov/vuln/detail/CVE-2022-48198
Wishing you all a very happy New Year! May your 2023 be filled with love and happiness.