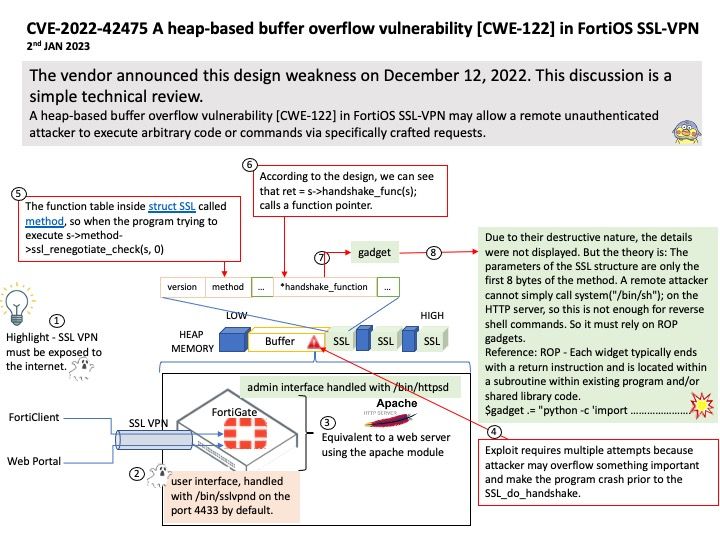
Preface: The SSL VPN must be exposed to the Internet. So you can use the service anywhere. This is a basic design.
Fortinet has patched a zero day buffer overflow in FortiOS that could lead to remote code execution. There has been a report of active exploitation and organizations should patch urgently. (2 weeks ago – Dec 12, 2022).
Background: Establish an SSL VPN from a client outside the base network to FortiGate inside the base network so that external clients can access the inside of the base network. You need to install the VPN client software called FortiClient on the external client.
Vulnerability details: A heap-based buffer overflow vulnerability [CWE-122] in FortiOS SSL-VPN 7.2.0 through 7.2.2, 7.0.0 through 7.0.8, 6.4.0 through 6.4.10, 6.2.0 through 6.2.11, 6.0.15 and earlier and FortiProxy SSL-VPN 7.2.0 through 7.2.1, 7.0.7 and earlier may allow a remote unauthenticated attacker to execute arbitrary code or commands via specifically crafted requests.
Official announcement: For details, see the link – https://www.fortiguard.com/psirt/FG-IR-22-398
Workaround: Disable SSL-VPN.