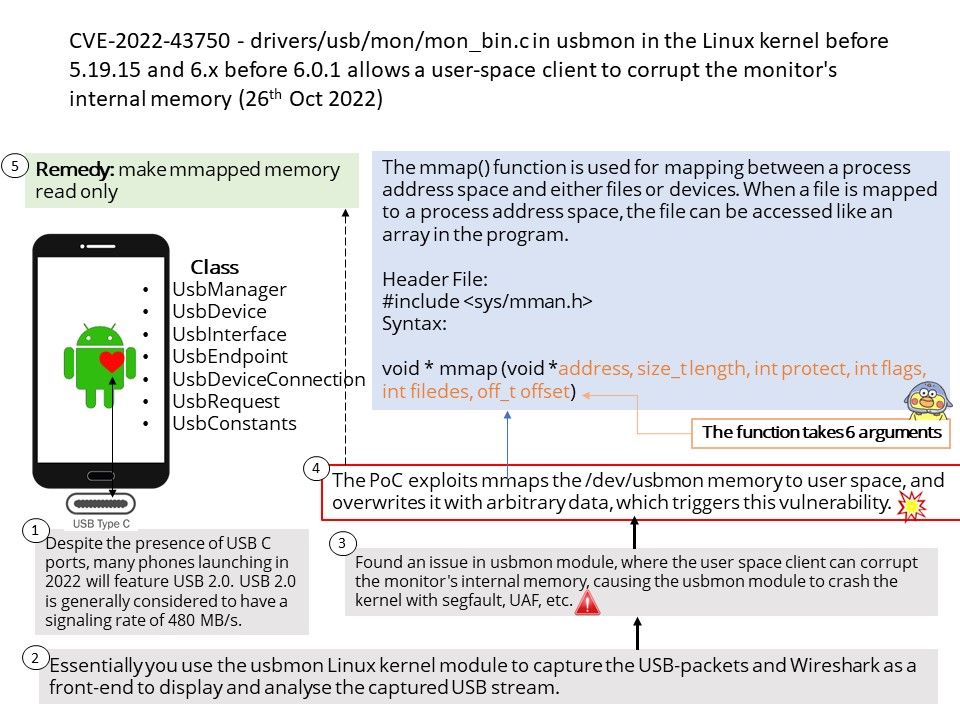
Preface: Despite the presence of USB C ports, many smartphones launching in 2022 will feature USB 2.0. USB 2.0 is generally considered to have a signaling rate of 480 MB/s.
Background: What is Usbmon in Linux? The name “usbmon” in lowercase refers to a facility in kernel which is used to collect traces of I/O on the USB bus. This function is analogous to a packet socket used by network monitoring tools such as tcpdump or Ethereal.
Vulnerability details: drivers/usb/mon/mon_bin[.]c in usbmon in the Linux kernel before 5.19.15 and 6.x before 6.0.1 allows a user-space client to corrupt the monitor’s internal memory. The weakness was disclosed 10/26/2022. The manipulation with an unknown input leads to a memory corruption vulnerability.
Reference: Found an issue in usbmon module, where the user space client can corrupt the monitor’s internal memory, causing the usbmon module to crash the kernel with segfault, UAF, etc.
The PoC exploits mmaps the /dev/usbmon memory to user space, and overwrites it with arbitrary data, which triggers this vulnerability.
Remedy: Upgrading to version 5.19.15 or 6.0.1 eliminates this vulnerability. The upgrade is hosted for download at cdn.kernel.org. Applying a patch is able to eliminate this problem. The bugfix is ready for download at git.kernel.org.
Official announcement: Please refer to the link for details – https://github.com/torvalds/linux/commit/a659daf63d16aa883be42f3f34ff84235c302198