Preface: When I read this CVE details. I found a gap between official “node JS” site announcements and security forums, including popular sites that post CVEs on a daily basis. In fact, if an attacker wants to trigger this vulnerability, it should meet the following requirements. That’s why I discuss this topic.
Background: Node[.] js can handle many concurrent requests. This is the main reason it quickly became popular among developers and large companies. Node js is faster than traditional java because it uses an asynchronous event-driven I/O model and does not have the overhead of the Java runtime environment. Node[.]js is a back-end JavaScript runtime environment. Node[.] js for Mobile Apps is a Node. js runtime that runs on Android and iOS, using the V8 JavaScript engine.
Ref: One of the most popular types of APIs for building microservices applications is known as “RESTful API” or “REST API.” Node[.]js runs on the V8 JavaScript Engine and executes JavaScript code outside a web browser. (Node[. ]js) propels communication among the parts of the applications (APIs of microservices) making it run faster.
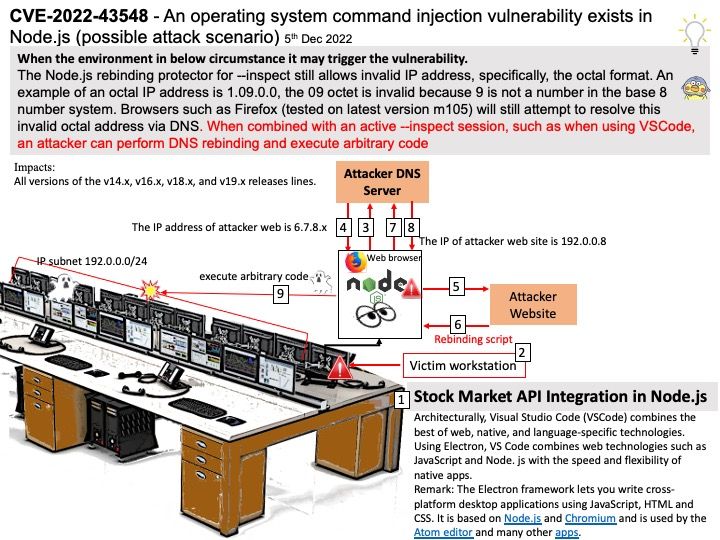
Vulnerability details: When the environment in below circumstance it may trigger the vulnerability.
The Node[.]js rebinding protector for –inspect still allows invalid IP address, specifically, the octal format. An example of an octal IP address is 1.09.0.0, the 09 octet is invalid because 9 is not a number in the base 8 number system. Browsers such as Firefox (tested on latest version m105) will still attempt to resolve this invalid octal address via DNS. When combined with an active –inspect session, such as when using VSCode, an attacker can perform DNS rebinding and execute arbitrary code.
Impacts: All versions of the 18.x, 16.x, and 14.x releases lines.
Official announcement: Please refer to the link for details – https://nodejs.org/en/blog/vulnerability/november-2022-security-releases/