Preface: A Xen guest typically has access to one or more paravirtualised (PV) network interfaces. These PV interfaces enable fast and efficient network communications for domains without the overhead of emulating a real network device.
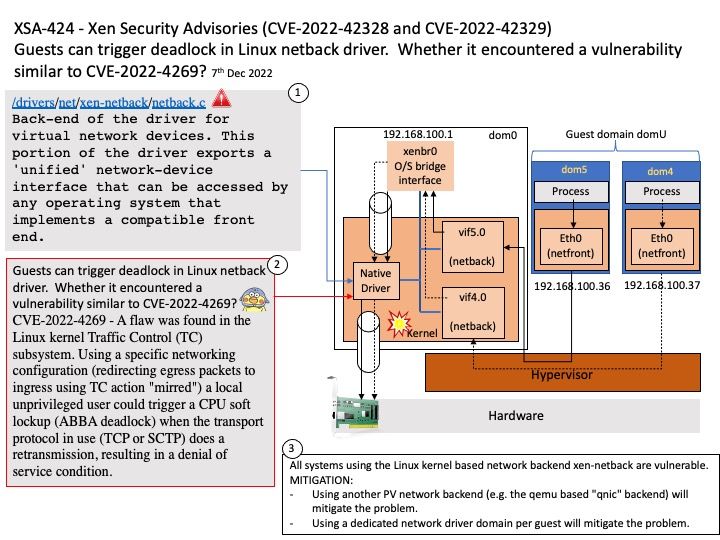
Background: XenServer can directly installs on bare-metal hardware without any restriction, overhead charge and performance obstacles of an Operating System. Device drivers from Linux kernel are used by means of XenServer. As the performance and production, it is capable to run on a wide range of storage devices and hardware. Remark: [/]drivers/[/]net[/]xen-netback[/]netback[.]c , Back-end of the driver for virtual network devices. This portion of the driver exports a ‘unified’ network-device interface that can be accessed by any operating system that implements a compatible front end.
Vulnerability details:
The patch for XSA-392 introduced another issue which might result in a deadlock when trying to free the SKB of a packet dropped due to the XSA-392 handling (CVE-2022-42328).
Additionally when dropping packages for other reasons the same deadlock could occur in case of netpoll being active for the interface the xen-netback driver is connected to (CVE-2022-42329).
IMPACT – A malicious guest could cause Denial of Service (DoS) of the host via the paravirtualized network interface.
RESOLUTION: Applying the attached patch resolves this issue (xsa424-linux.patch Linux 6.0, 6.1-rc).
Official announcement: Please refer to the link for details – http://xenbits.xen.org/xsa/advisory-424.html