Preface: Capturing and replaying a couple of signals are-synchronizes the rolling codes and unlocks most of today’s vulnerable vehicles.
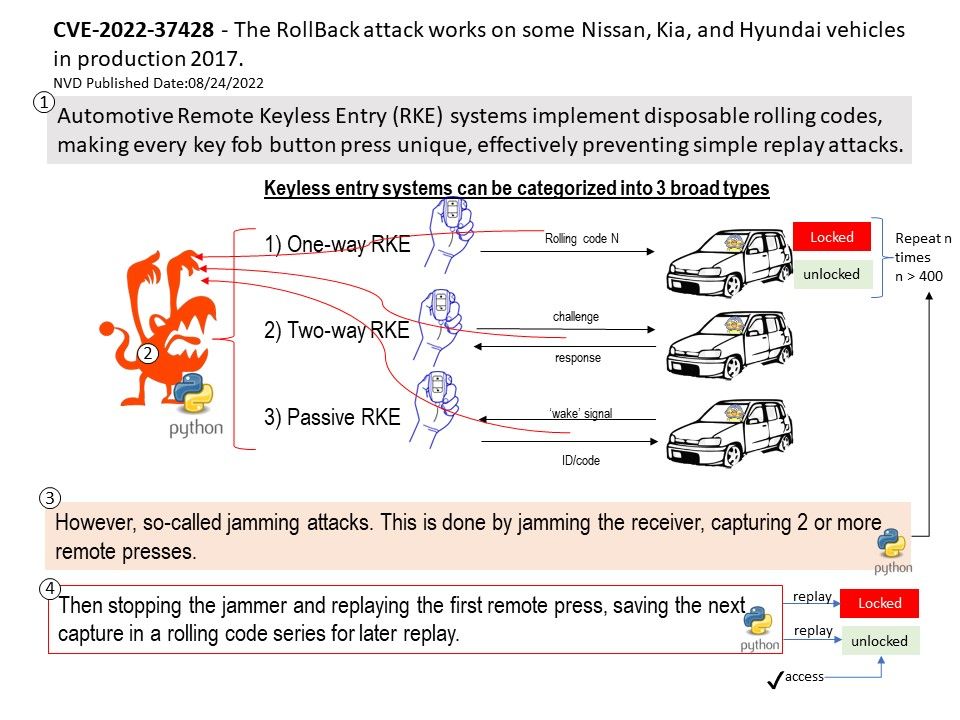
Background: Automotive Remote Keyless Entry (RKE) systems implement disposable rolling codes, making every key fob button press unique, effectively preventing simple replay attacks. However a attack so called jamming. This is done by jamming the receiver, capturing 2 or more remote presses, then stopping the jammer nd replaying the first remote press saving the next capture iin the rolling code series to replay later.
Remark: So far, the root cause is not confirmed and no explicit mitigation exists, said Blackhat conference 2022 .
Vulnerability details: The Remote Keyless Entry (RKE) receiving unit on certain Nissan, Kia, and Hyundai vehicles through 2017 allows remote attackers to perform unlock operations and force a resynchronization after capturing two consecutive valid key fob signals over the radio, aka a RollBack attack. The attacker retains the ability to unlock indefinitely.
Official announcement: Refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-37418