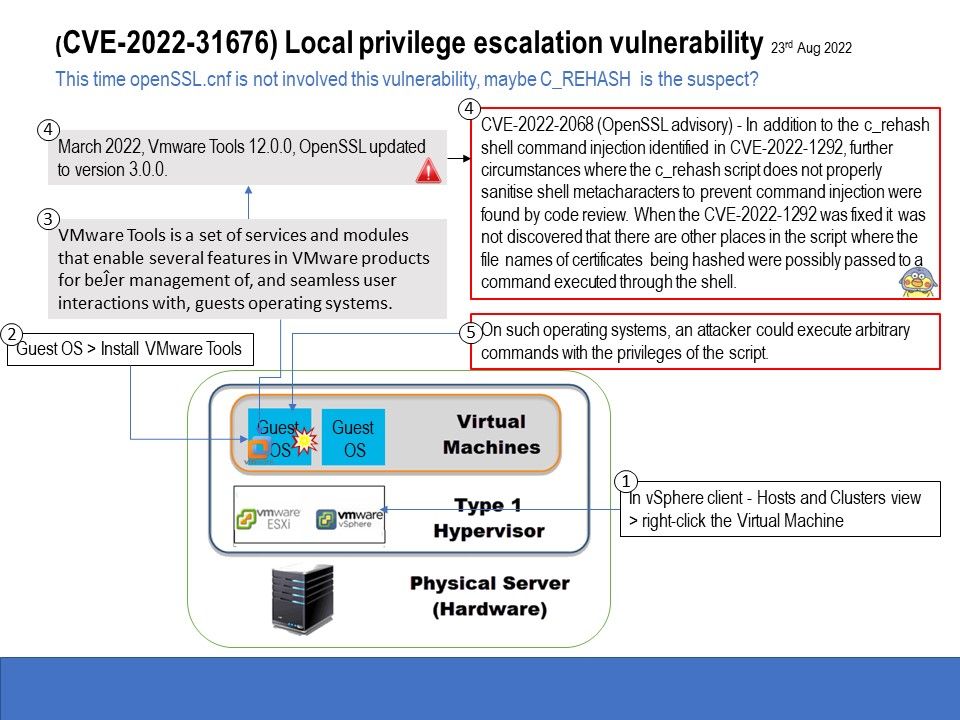
Preface: This time openSSL.cnf is not involved this vulnerability, maybe C_REHASH is the suspect?
Background: VMware Tools is a set of services and modules that enable several features in VMware products for better management of, and seamless user interactions with, guests operating systems.
Some VMware Tools seĴings might expose security risks. For example, VMware Tools enables you to
connect virtual devices such as serial and parallel ports to virtual machines. A connected device might be a potential channel of attack.
When serial port access is enabled for a VM instance, clients can attempt to connect to that instance from any IP address and this allows anybody to access the instance if they know the user name, the SSH key, the project ID, and the instance name and zone.
Vulnerability Details: A malicious actor with local non-administrative access to the Guest OS can escalate privileges as a root user in the virtual machine , said VMware. Please refer to the link for details – https://www.vmware.com/security/advisories/VMSA-2022-0024.html
My observation: Since the vendor didn’t describe what the actual reason was. A hints for my analysis is based on openssl 3.0 working with VMware Tools 3.0.0 written in offical article. Coincidentally, a bug was discovered in OpenSSL 3.0.0, which was released in June 2022. The flaw will be fixed on OpenSSL 3.0.4. Affected products include 3.0.0, 3.0.1, 3.0.2, and 3.0.3. If you are interested in this, please refer to the attached image.