Preface: The X-Forwarded-For request header is automatically added and helps you identify the IP address of a client when you use an HTTP or HTTPS load balancer. Because load balancers intercept traffic between clients and servers, your server access logs contain only the IP address of the load balancer. To see the IP address of the client, use the X-Forwarded-For request header.
Background: The observiced service daemon provides a wide variety of services. It runs continually on the administrative server, media server, and client. On the administrative server, observiced runs jobs at the request of the schedule daemon, cleans up log files and transcripts, and provides access to Oracle Secure Backup configuration data to other hosts in the domain.
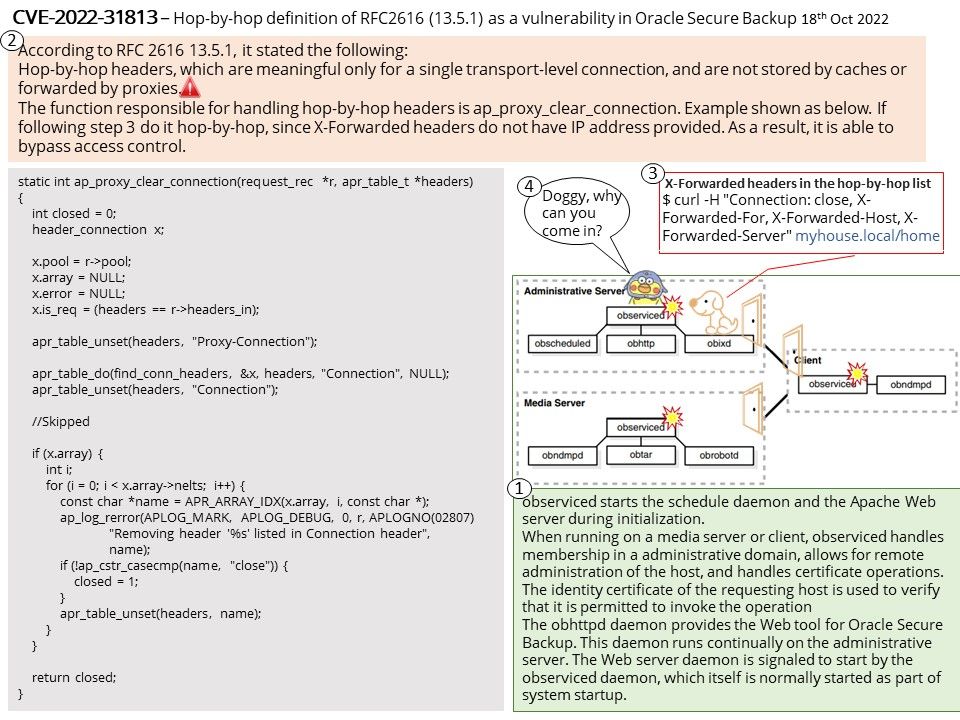
observiced starts the schedule daemon and the Apache Web server during initialization.
When running on a media server or client, observiced handles membership in a administrative domain, allows for remote administration of the host, and handles certificate operations. The identity certificate of the requesting host is used to verify that it is permitted to invoke the operation
The obhttpd daemon provides the Web tool for Oracle Secure Backup. This daemon runs continually on the administrative server. The Web server daemon is signaled to start by the observiced daemon, which itself is normally started as part of system startup.
Vulnerability Details: Apache HTTP Server 2.4.53 and earlier may not send the X-Forwarded-* headers to the origin server based on client side Connection header hop-by-hop mechanism. This may be used to bypass IP based authentication on the origin server/application.
Additional CVEs addressed are:The patch for CVE-2022-31813 also addresses CVE-2022-26377, CVE-2022-28614, CVE-2022-28615, CVE-2022-29404, CVE-2022-30522, and CVE-2022-30556.
According to RFC 2616 13.5.1, it stated the following:
Hop-by-hop headers, which are meaningful only for a single transport-level connection, and are not stored by caches or forwarded by proxies.
If following step 3 in attached diagram do it hop-by-hop, since X-Forwarded headers do not have IP address provided. As a result, it is able to bypass access control.
Official announcement: Oracle Critical Patch Update Bulletin – October 2022 has been released. See the link for details – https://www.oracle.com/security-alerts/cpuoct2022.html