Preface: Touchscreens provide direct navigation and accessibility through physical touch controls, eliminating the need for traditional computer mice and keyboards.
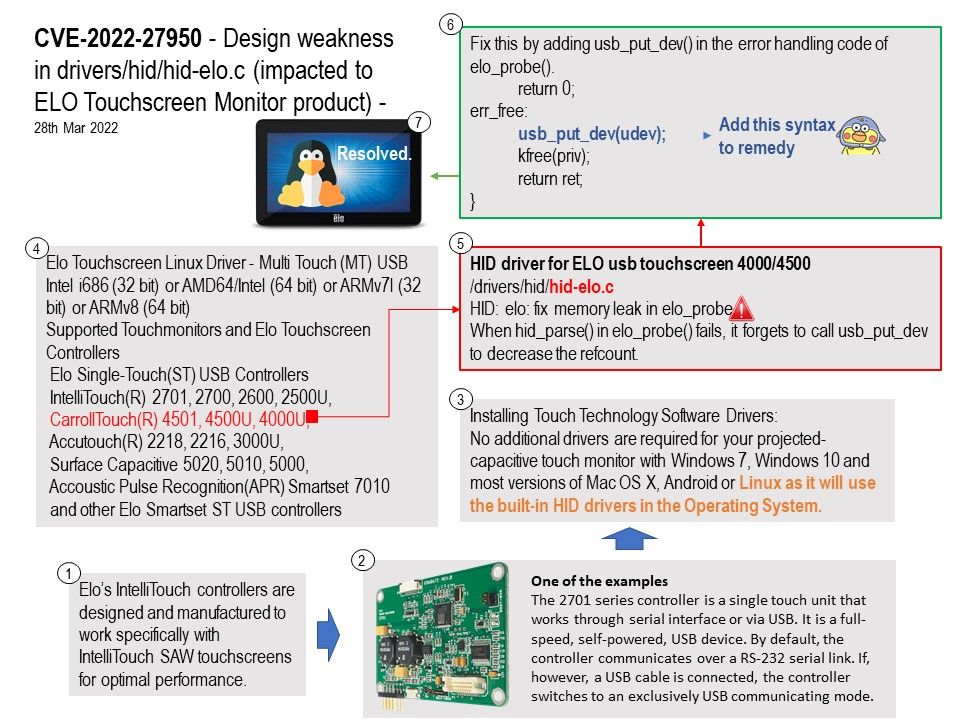
Background: Touchscreens are common in devices such as game consoles, personal computers, electronic voting machines, and point-of-sale (POS) systems. Elo’s IntelliTouch controllers are designed and manufactured to work specifically with IntelliTouch SAW touchscreens for optimal performance. No additional drivers are required for your projected-capacitive touch monitor with Windows 7, Windows 10 and most versions of Mac OS X, Android or Linux as it will use the built-in HID drivers in the Operating System.
Come from Linux Operating system the driver (hid-elo[.]c) located in drivers/hid subdirectory. It is compatible with ELO controller (single touch unit) that works through serial interface or via USB. This hardware controller is a full-speed, self-powered, USB device. By default, the controller communicates over a RS-232 serial link. If, however, a USB cable is connected, the controller switches to an exclusively USB communicating mode.
Vulnerability details: In drivers/hid/hid-elo[.]c in the Linux kernel before 5.16.11, a memory leak exists for a certain hid_parse error condition. When hid_parse() in elo_probe() fails, it forgets to call usb_put_dev to
decrease the refcount.
Remedy: Fix this by adding usb_put_dev() in the error handling code of elo_probe(). For details, please refer to attached diagram.
Recommendation: Update to driver v5.17-rc5