Preface: Security misconfiguration can happen at any level of an application stack, including the network services, platform, web server, application server, database, frameworks, custom code, and pre-installed virtual machines, containers, or storage. Automated scanners are useful for detecting misconfigurations, use of default accounts or configurations, unnecessary services, legacy options, etc.
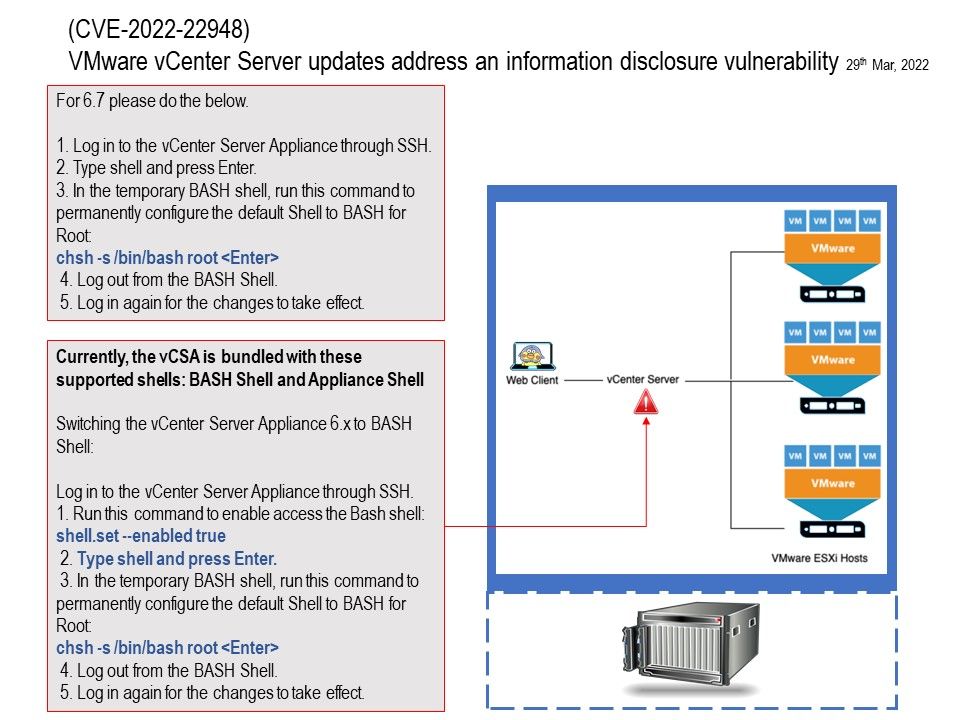
Background: vSphere is a product suite. ESXi is a hypervisor installed on the physical machine. vCenter Server is a management platform for VMs. When you are working on a small virtualization environment, the vSphere client will be sufficient enough to maintain and manage virtual machines hosted on a few ESXi servers.
Vulnerability details: The vCenter Server contains an information disclosure vulnerability due to improper permission of files. VMware has evaluated the severity of this issue to be in the Moderate severity range with a maximum CVSSv3 base score of 5.5.
Likelihood – Remediation related to this vulnerability (see below):
Switching the vCenter Server Appliance 6.x to Appliance Shell
Log in to the vCenter Server Appliance through SSH.
Run this command to change from using the BASH Shell to the Appliance Shell:
chsh -s /bin/appliancesh root
Log out from the Appliance Shell.
Log in again for the changes to take effect.Vendor announcement : Please refer to the link for details – https://www.vmware.com/security/advisories/VMSA-2022-0009.html