Preface: Hacking using RF tools due to RF transmit power limiting capabilities. From a technical point of view, it is similar to a short-range attack. Compared to traditional network attacks that run on top of TCP/IP networks. Network-based cyberattacks will be more disruptive because they are not limited to a single device.
Background: The following attacks can be performed on the radio communication component of any IoT device.
Utilize tools to capture the raw data transmitted to the IoT device and attack. This is so called a replay attack. Since the raw data is played back to the IoT device to perform the actual attack. Whereby, this is the most common method for cyber expert to dig out the cyber security matter.
Tools used – HackRF, BladeRF, RTL-SDR, FUNcube dongle, GQRX, SDR#, URH, etc.
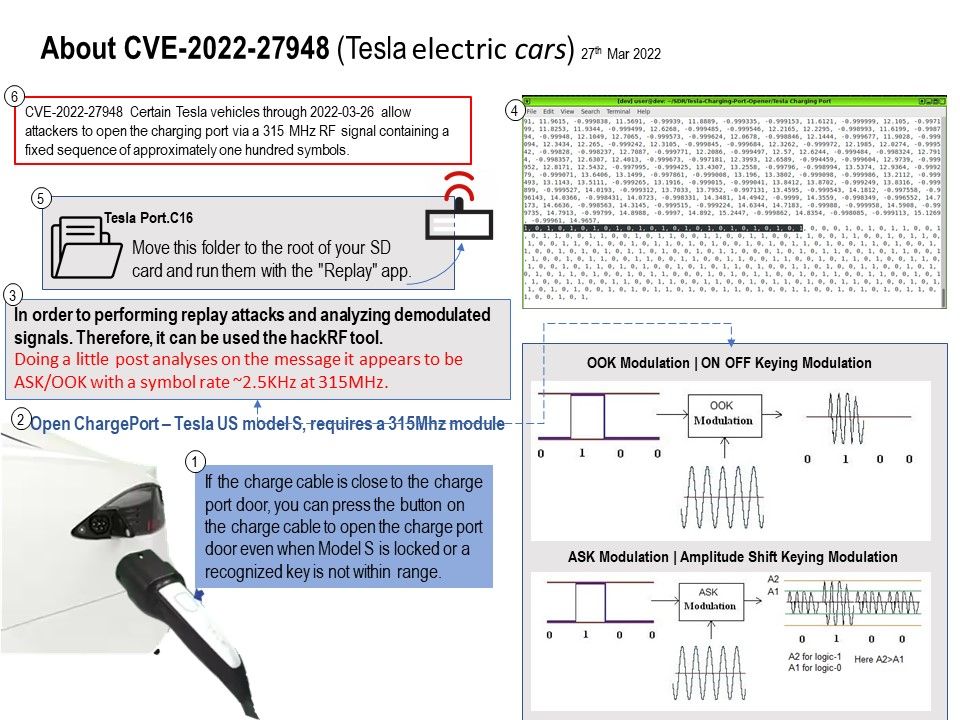
Vulnerability details: Certain Tesla vehicles through 2022-03-26 allow attackers to open the charging port via a 315 MHz RF signal containing a fixed sequence of approximately one hundred symbols.
According to the security expert findings. Doing a little post analyses on the message it appears to be ASK/OOK with a symbol rate ~2.5KHz at 315MHz. Once the data is analyzed and processed, it will obtained the binary data including center frequency and the Modulation scheme that is being used. Then attacker will use the reserve engineering. Exploiting RFtool sent back original data to the IoT device for launching the actual attack. This kind of attack is complicated to perform when compared to the replay attack.
Remark: Tesla US model S, requires a 315Mhz module.
Observation: According to the original design. If the charge cable is close to the charge port door, you can press the button on the charge cable to open the charge port door even when Model S is locked or a recognized key is not within range. About eight years ago, a technical expert found that when you use Type 2 charge cable on Tesla model S. The auto sense function cannot open the charge port door. In additional, he discovered that available data memory divided into Bank 0-15. Each Bank may contain Special Function Registers, General Purpose Registers, and Access RAM .
As a result, it looks that the existing design do not have tight protection in this area. Therefore, it is possible make use of a 315Mhz transmitter send the original function.
It looks that this design weakness require vendor enhancing the protection of this feature in this area.
Details of Design Weaknesses: Please refer to the link – https://github.com/pompel123/Tesla-Charging-Port-Opener