Preface: A lot of people will familiar with Rapid 7 (metasploit), it is a powerful penetration test tools in existing market. If the product only provide a penetration test tool in today demanding market. It is limited the business development. However, from my personal point of view, SIEM and log management functions by Rapid 7 is a new area to me. Perhaps this is not new product.
Background: The universal Insight Agent is lightweight software you can install on any asset—in the cloud or on-premises—to collect data from across your IT environment. With unified data collection, security, IT, and DevOps teams can collaborate effectively to monitor and analyze the environments. View endpoint data is one of the powerful feature, it including: detailed asset information, Windows registry information, file version and package information, running processes, authentication information, local security and event logs. As a agent based design, so it is compatible with Linux, Mac and windows. Vendor claimed that the agent footprint is small. Apart from that memory consumption is low.
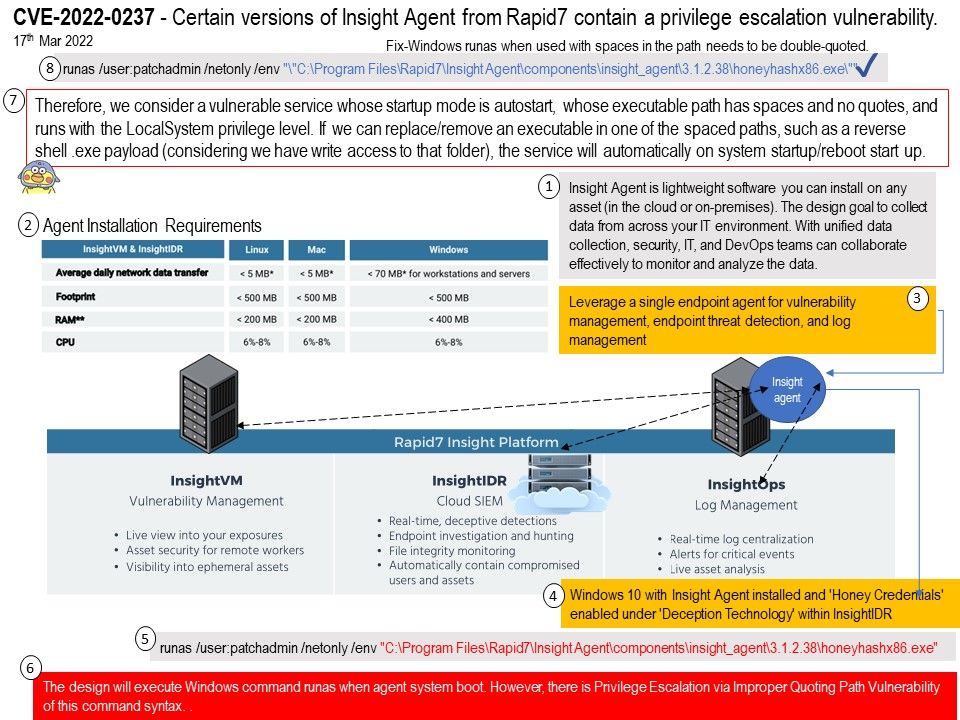
Vulnerability details: When security expert utilizing procmon boot-logging, it give a seen to him found that the call for ‘Program.exe’ via command line utilizing Windows ‘runas’ only single-quoted. Rapid7 Insight Agent versions 3.1.2.38 and earlier suffer from a privilege escalation vulnerability, whereby an attacker can hijack the flow of execution due to an unquoted argument to the runas.exe command used by the ir_agent.exe component, resulting in elevated rights and persistent access to the machine.
Remedy: Fix-Windows runas when used with spaces in the path needs to be double-quoted. Please refer to attached diagram (point 8)
Vendor announcement: For details, please refer to the link – https://docs.rapid7.com/release-notes/insightagent/20220225/