Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
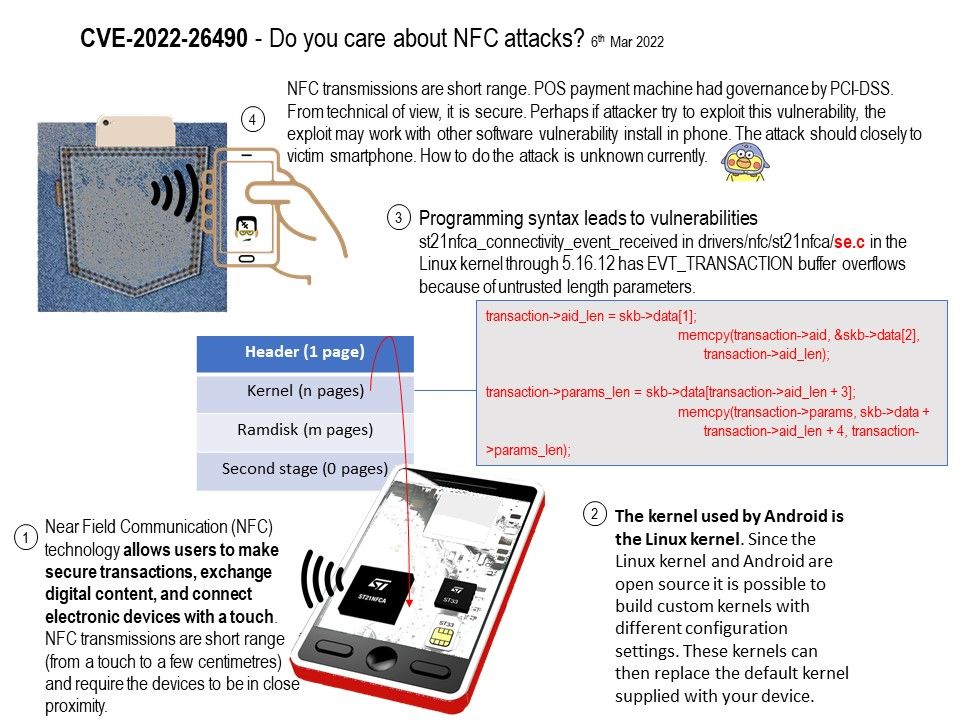
Background: The ST21NFCA is a single chip designed for supporting 13.56 MHz contactless communication, including Near Field Communication (NFC) functions in the three operating modes: card emulation, reader and peer-to-peer communication. Furthermore, it is a system on chip solution able to be compliant with NFC communication
system embedded in a mobile phone.
The kernel used by Android is the Linux kernel. Since the Linux kernel and Android are open source it is possible to build custom kernels with different configuration settings. These kernels can then replace the default kernel supplied with your device.
Vulnerability details: st21nfca_connectivity_event_received in drivers/nfc/st21nfca/se.c in the Linux kernel through 5.16.12 has EVT_TRANSACTION buffer overflows because of untrusted length parameters.
Ref: EVT_TRANSACTION. This event notifies the terminal host that it shall launch an application associated to an NFC application in a UICC host.
It appears that there are some buffer overflows in EVT_TRANSACTION.This happens because the length parameters that are passed to memcpy come directly from skb->data is not protected in any way.
Remedy: For more details, please refer to the link – https://github.com/torvalds/linux/commit/4fbcc1a4cb20fe26ad0225679c536c80f1648221