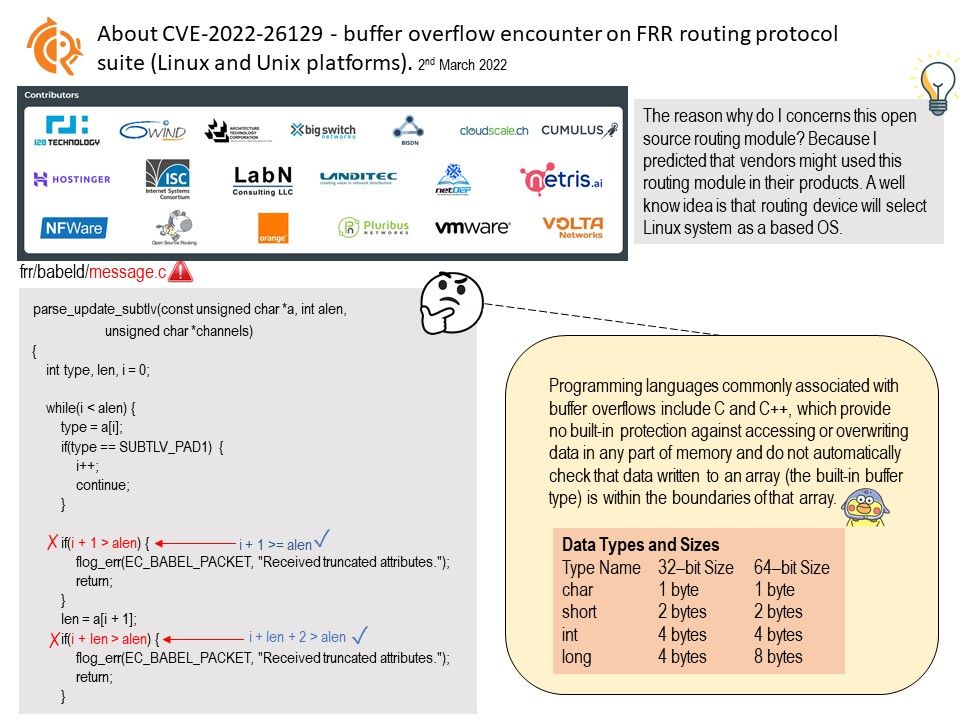
Preface: The reason why do I concerns this open source routing module? Because I predicted that vendors might used this routing module in their products. A well know idea is that routing device will select Linux system as a based OS.
Background: FRRouting (FRR) is a free and open source Internet routing protocol suite for Linux and Unix platforms. It was created as a fork from Quagga. FRRouting is distributed under the terms of the GNU General Public License v2 (GPL2). It implements BGP, OSPF, RIP, IS-IS, PIM, LDP, BFD, Babel, PBR, OpenFabric and VRRP, with alpha support for EIGRP and NHRP. FRR is a large project developed by many different groups.
Vulnerability details: Buffer overflow vulnerabilities exist in FRRouting through 8.1.0 due to wrong checks on the subtlv length in the functions, parse_hello_subtlv, parse_ihu_subtlv, and parse_update_subtlv in babeld/message[.]c.
Informed by related party that there are two programming syntax which causes design weakness.
Line 143: the condition should be i + 1 >= alen instead of i + 1 > alen. Otherwise, overflows will happen at 147.
Line 148: the condition should be i + len + 2 > alen instead of i + len > alen. We need include extra two bytes, a[i] and a[i + 1] in this check.
Additional information: Int, short for “integer,” is a fundamental variable type built into the compiler and used to define numeric variables holding whole numbers. Other data types include float and double. C, C++, C# and many other programming languages recognize int as a data type.
Under the C++ standard, what you are doing is undefined behavior. The memory layout of unsigned and signed ints is not guaranteed.
Status: In the moment, no vendors claim that there products was impacted by this package/module. Let’s keep our eye open to see whether there are security updates in this matter.