Preface: You use a method that takes an array of bytes. But you don’t know how big this array is, but it’s controlled by the code calling the method. Let’s assume it is 500 bytes long. Then you read an integer from somewhere else, let’s assume 1000 is read.
As a result, you attempt to read 1000 bytes into an array that can only hold 500 bytes, you perform no checking to make sure your array is it big enough, nor do you attempt to read in chunks and concatenate if it’s not big enough. So an error display in log event activtites. Whereby, the system halted.
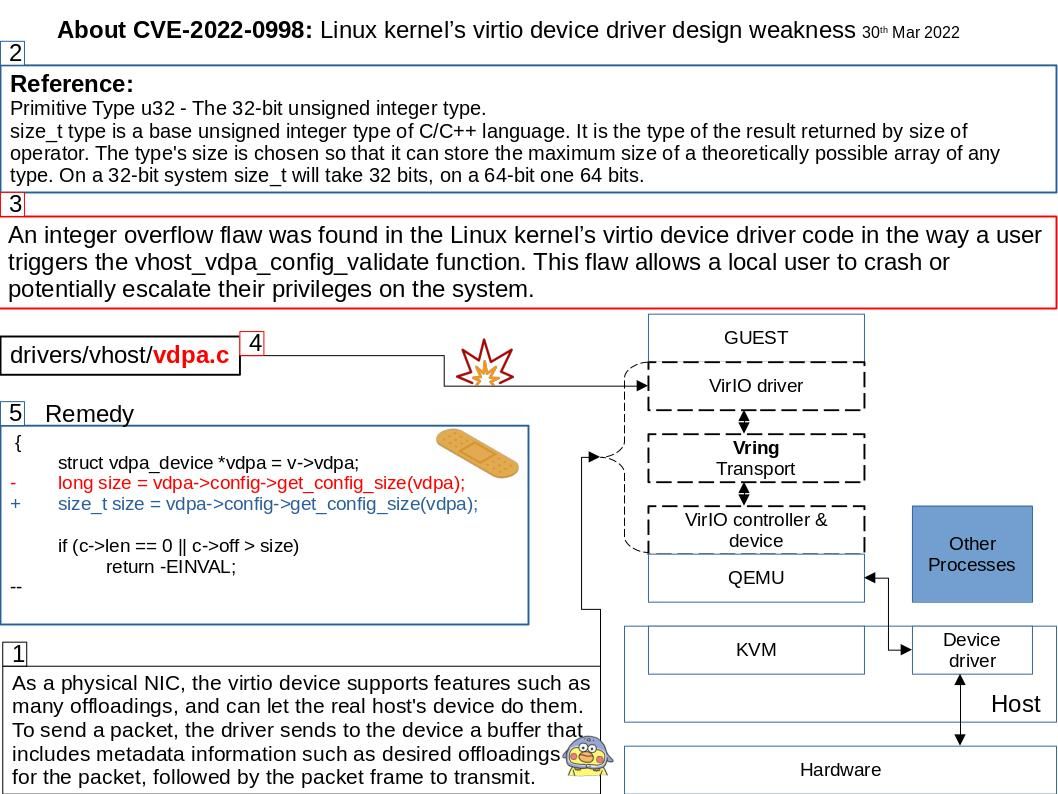
Background: KVM (Kernel-based Virtual Machine) is a FreeBSD and Linux kernel module that allows a user space program access to the hardware virtualization features of various processors, with which QEMU is able to offer virtualization for x86, PowerPC, and S/390 guests.
Virtio is a virtualization standard for network and disk device drivers where just the guest’s device driver “knows” it is running in a virtual environment, and cooperates with the hypervisor. As a physical NIC, the virtio device supports features such as many offloadings, and can let the real host’s device do them. To send a packet, the driver sends to the device a buffer that includes metadata information such as desired offloadings for the packet, followed by the packet frame to transmit.
Vulnerability details: An integer overflow flaw was found in the Linux kernel’s virtio device driver code in the way a user triggers the vhost_vdpa_config_validate function. This flaw allows a local user to crash or potentially escalate their privileges on the system.
Official announcement – about their troubleshooting: The added ‘c->off > size’ test in that commit will be done as an unsigned comparison on 32-bit (safe due to not being signed).
On a 64-bit platform, it will be done as a signed comparison, but in that case the comparison will be done in 64-bit, and ‘c->off’ being an
u32 it will be valid thanks to the extended range (ie both values will be positive in 64 bits).
So this was a real bug, but it was already addressed and marked for stable. For more details, please refer to the link – https://lore.kernel.org/netdev/20220123001216.2460383-13-sashal@kernel.org/
Reference: Primitive Type u32 – The 32-bit unsigned integer type.
size_t type is a base unsigned integer type of C/C++ language. It is the type of the result returned by size of operator. The type’s size is chosen so that it can store the maximum size of a theoretically possible array of any type. On a 32-bit system size_t will take 32 bits, on a 64-bit one 64 bits.